Are you keen to learn Microsoft’s Active Directory concepts every Systems Administrator must know? This guide introduces you to AD and concepts like DCs, Forests and the rest.
Overview
Active Directory (AD) is a Microsoft directory service that stores information about objects in a network. AD also makes it easy for the stored data to be accessed by authorized users.
Examples of Active Directory objects are users, computers, printers and other resources in a network.
A user has to be authenticated before the user is allowed to logon to an AD network. Authentication is usually achieved by verifying the users username and password.
After a user logs on to the network Active Directory stores information about the users permissions (group memberships, etc) and access rights. When the user requests access to a resource, AD grants or denies access. The process of granting or denying access is called Authorization.
This tutorial will cover the main concepts of AD, including its physical and logical structure. It will also cover Domain Controllers, AD Schema, Forest and Domain. Some other concepts you will learn include Replication, Domain Controller Roles (Operations Master Roles), Global Catalog servers, Universal Group Membership Caching and Read-Only Domain Controllers.
By the time you complete this tutorial you can confidently discuss how Active Directory works and understand its major concepts. Finally, you will learn some tasks you can perform with Active Directory Users and Computers, Sites and Services, Domains and Trusts and more.
Some Important Active Directory Concepts
Active Directory has some very important concepts that you need to understand to effectively deploy and manage it. Here are some of the essential concepts:
AD Domain Controller
An AD Domain Control (AD DC) is a Windows Server running AD Domain Services. For a Windows Server to run AD DC service it has to be promoted to a Domain Controller using Server Manager. Later in this tutorial, you will learn how to promote a Windows Serer to a Domain Controller.
Active Directory Schema
Next important concept is AD Schema. AD Schema defines object classes and their attributes. An example of a AD object class is a user. A user has some attributes like the users name, manager, etc.
AD stores objects classes and their attributes using AD schema. Active Directory Schema has standard objects like users, computers, printers, etc. However, if you require additional objects, you could extend the schema. As an example you will need to extend AD schema before you install Microsoft Exchange or SCCM.
To see how you can extend the AD schema, see Extend the Schema in the Additional Resources and References at the end of this tutorial.
Active Directory Forest
In the AD hierarchical structure, the Forest is at the top of the logical structure of AD. The next level of the hierarchy are Domains, then you have Organization Units (OUs). Within OUs you have users and computers.
Consequently, an AD Forest contains a number of AD Domains interconnected by Trust Relationship. Below is a simple illustration of an AD Forest hierarchy. To read more about AD Forest, visit What is an Active Directory Forest?
When you Create Trusts between two domains in a Forest users in one domain can be authenticated by the trusted domain. Also, resources can also be accessed between domains with a Trust relationship.
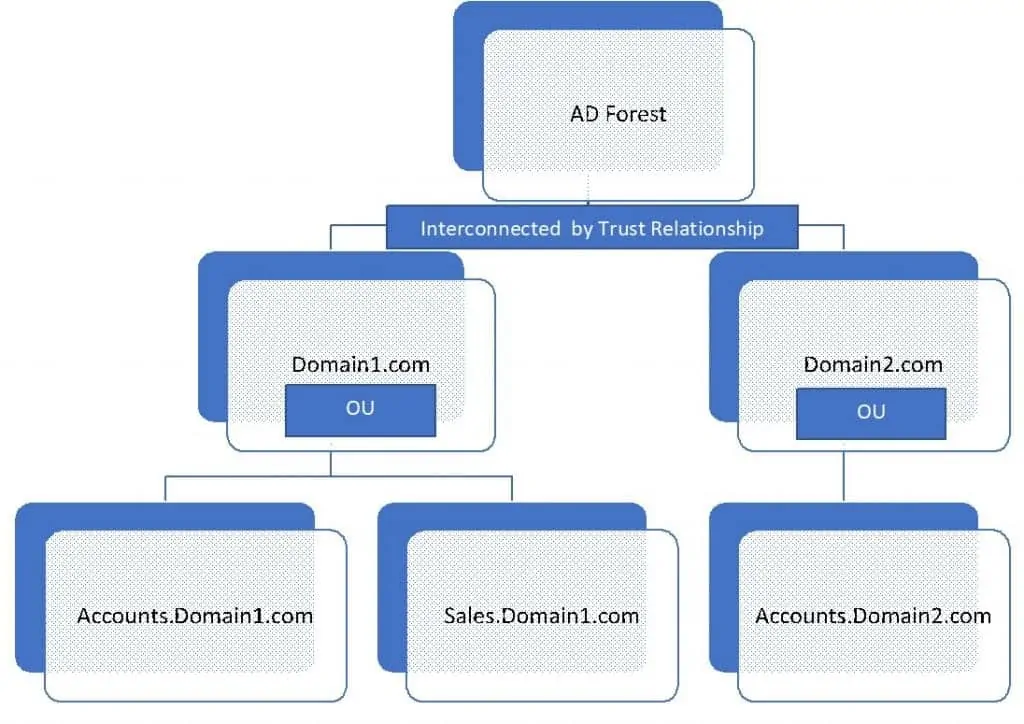
Types of AD Trusts
You can create 4 types of Trust relationships in an AD Forest – external, forest, shortcut, and realm trusts. To read more about AD Trusts, open Advanced Active Directory Infrastructure for Windows Server 2012 R2 Services.
AD Domain
AD Domain is the next level to Forests in the hierarchy. An AD Domain contains a collection of objects. For example, Users and Computers. Domains are identified by their DNS names, for example, Domain1.com, Domain2.com.
The DNS Names of AD Domains do not have to end in .com, they could also end in .local for example.
Active Directory Sites
AD sites configuration usually follow physical network subnets. Replication configuration within sites is usually different from the configuration between sites.
As an example, if you have 2 Domain Controllers within the same network subnet, you could configure replication between them to be optimized for speed.
AD Replication
If you deploy Active Directory in a production environment, it is recommended to have at least 2 Domain Controllers (DCs) in your AD Domain. The reason for this is obvious – create redundancy.
Before I proceed let me mention that AD operates what is called a multi-master model. Meaning that all Domain Controllers (DCs) within the domain contains writable copies of objects. As you will see later, there are some exceptions to this rule.
The fact that objects can be created in any DC means there is need for replication between the Domain Controllers. The process of created objects in one DC syncing or updating to other DCs is know as Replication.
Read more about AD replication by clicking the Active Directory Replication In Depth link on the Additional Resources and References section.
Active Directory Operations Masters
In the previous section, I mentioned that though Active Directory operates a multi-master model, there are exceptions to this rule.
There are certain tasks within an AD Domain that has to be be completed using the single-master model. That is, one Domain Controller is designated the role of handling the task.
The primary reason for the single-master model is to avoid conflicts. Due to the nature of the single-master roles, if more than one DC were to handle the task at the same time, it will create conflict. You will understand this better when you read the 5 Operations Master roles to be discussed shortly.
Below are the 5 Active Directory Flexible Single Master Operations (FSMO) Roles.
Schema Master
Earlier in this tutorial, I discussed AD Schema. I said that an Active Directory Schema defines object classes and their attributes. I also said that sometimes you may want to create additional AD AD Schema classes by extending the Schema.
The DC responsible for updating the Schema is called the Schema Master. When the Schema Master updates the Schema, it replicates the update to other DCs. There is one Schema Master in a Directory – this DC is know as the Schema Master.
Domain Naming Master
The DC assigned the Domain Naming Master FSMO role is responsible for adding or deleting domains in the forest-wide domain name space.
The Domain Naming Master DC is also responsible for adding or removing cross references to domains in external directories.
RID Master
Whenever a Domain Controller creates a security principal for example a user or a computer, the DC assigns the object a unique Security ID (SID). The SID is made up of a Domain SID and a Relative ID (RID). The Domain SID is the same for all objects created in the domain while the RID is unique for each security principal created.
Every DC has a pool of RIDs assigned to it. The DC responsible for allocating RID pools to other DCs is the RID Master.
The PDC Emulator Master
The DC that holds the PDC Emulator role is responsible for authenticating users, synchronizing password changes and also responsible for time synchronization.
It also manages account lockouts and forwards authentication failures due to incorrect passwords to other DCs.
Infrastructure Master (IM)
In a multi-domain AD forest, the DC assigned the Infrastructure Master FSMO role is responsible for keeping cross-domain object references up to date.
As an example, say an object in Domain 1 is referenced by another object in Domain 2. When the referenced object is modified the IM is responsible for updating the references.
In conclusion, before I discussed the 5 FSMO Active Directory DC roles, I said that AD operates a multi-master model. That is, all DCs contains writable copies of the AD database.
I also said that though in an AD domain, despite the multi-maser model, some tasks can only be performed via a single-master operations model. Thus the 5 FSMO roles.
Having said that, now that you know the 5 single-master operations roles, I hope it is easy to see why an RID pool for example can only be assigned by only one DC. If 2 DCs were to assign RID pools to other Domain Controller, there is a risk of overlap and two different objects may then have the same RID.
The same augment applies to the other 4 FSMO roles discussed earlier.
Global Catalog Servers (GC)
To understand the role of the Global Catalog Server, I will refer you to what I said earlier about Active Directory Forests. An AD Forest contains a number of AD Domains interconnected by Trust Relationships.
With that in mind, for every domain within the forest, all DCs stores data about every object within its own domain. As I pointed out earlier, within an AD forest, there may be need for cross-domain object referencing. For this to work effectively, a DC is assigned the role of GC to store information about ALL objects within the Forest.
If you relate this to the the IM FSMO role discussed earlier, it becomes easy to see why an Infrastructure Master will need to constantly communicate with a GC server. This is so it receives updates about cross-domain object references.
The Infrastructure Master is responsible for updating cross-object references within an AD Forest. The Global Catalog Server holds information about ALL objects within the Forest. It makes logical sense for the Infrastructure Master to receive object cross-referencing information from a GC Server.
Therefore, it is NOT recommended for one DC to be assigned the role of a GC Server and an Infrastructure Master role except:
- There is only one domain in the forest – in this situation the same DC will be responsible for all roles.
- Every DC in the domain is a global catalog server
Universal Groups Membership Caching
By default universal group memberships information are only stored in Global Catalog servers. For this reason, in a multi-domain AD Forest (where universal groups are present) if a user logs on to the domain for the first time, a GC server must be available for the logon to be processed.
For small AD Sites without a GC Server, other DCs may be enabled to store universal group membership information. This is achieved by enabling Universal Groups Membership Caching (UGMC) in the AD Site.
UGMC is enabled on per site basis. When enabled in an AD site, all DCs in the site will participate.
Read-Only Domain Controllers (RoDCs)
In this tutorial, I already said that all DCs in an AD Domain are writable. That said, there are certain situations where you may want to install (RoDCs).
A typical situation may be in a remote site with limited physical security for DCs in that location. Under this circumstance you may want to install a DC that can only read AD data but cannot write to or update any object.
RoDCs are only available in Windows Server 2008 and higher.
Physical and Logical Structure of Active Directory
So far I have covered a number of important Active Directory concepts. In this section I will be discussing two other important concepts in AD – physical and logical structures of Active Directory.
Physical Structure of AD
“Physical structure” entails things you can touch and feel. Therefore, the physical structure of AD are Domain Controllers and network Sites.
The tools you require to manage the physical structure of Active Directory Active Directory Sites and Services. Later in this tutorial I will discuss the tasks you can perform with AD Sites and Services.
Logical Structure of Active Directory
Compared to the physical structure of AD, the logical structure is “virtual”. The components that make up the logical structure of AD are: forests, trees, domains, OUs and global catalogs. To get detailed definitions of forests, trees, domains, OUs and global catalog, click Questions About Active Directory Infrastructure.
Active Directory Administration
So far we have covered some important concepts of AD. This section is about administering Active Directory. I will be discussing the following AD tools:
- Active Directory Users and Computers
- AD Sites and Services
- Active Directory Domains and Trusts
- AD PowerShell Module
- Group Policy Management Console (GPMC)
Active Directory Users and Computers
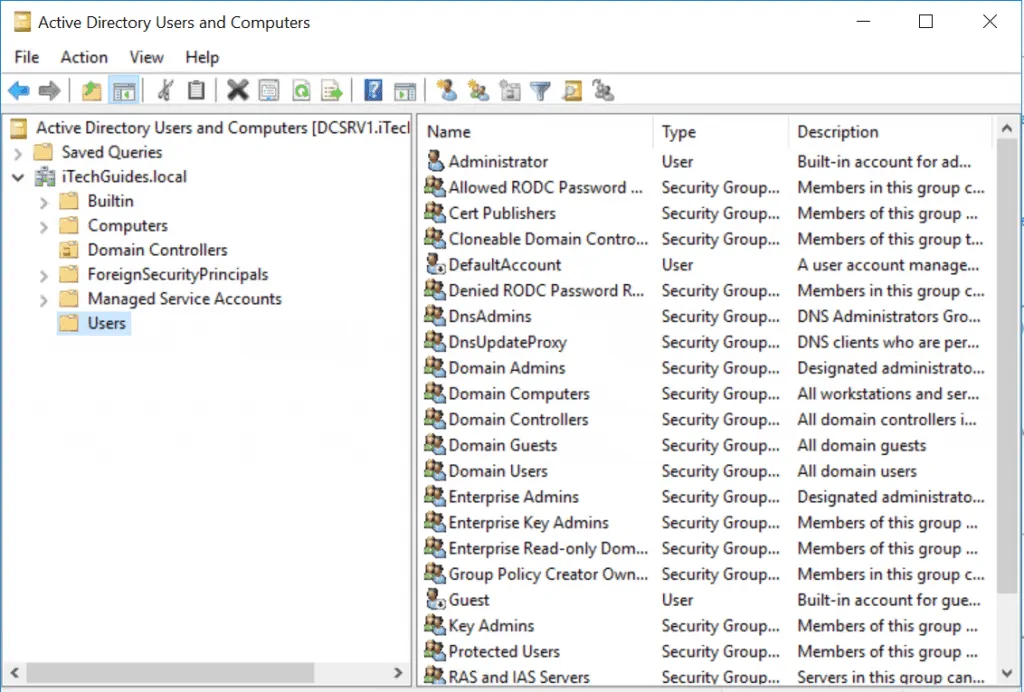
This is one of the most used AD tools. With AD Users and Computers, you can:
- Create Organizational Units
- Create Containers
- Delegate Authorities
- Create Users
- Transfer RID, PDC and Infrastructure FSMO Roles
- Run Queries
- Raise Domain Functional Levels
AD Sites and Services
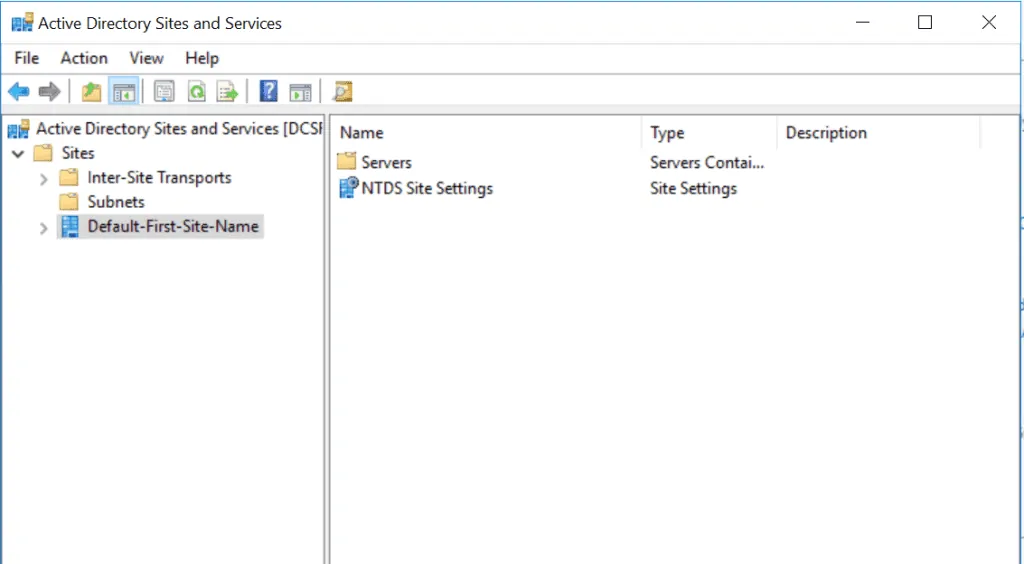
As you get more comfortable with Active Directory administration, you will start working with Sites and Services.
You can perform the following tasks with AD Sites and Services tool:
- Enable Universal Group Membership Caching (UGMC)
- Configure Inter-Site Transports
- Create new AD Site connections
- Delegate Control to existing Sites
- Create Subnets
Active Directory Domains and Trusts
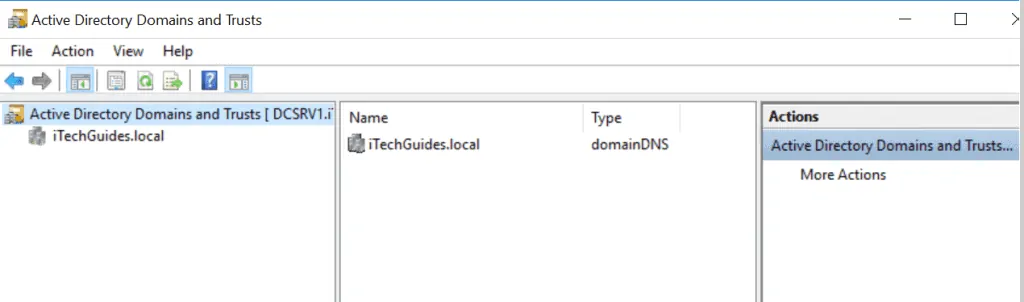
This tool is used to perform some of the most advanced admin functions in AD. Below are some of the tasks you can complete with Active Directory Domains and Trusts:
- Raise Forest Functional level
- Transfer Domain Naming Master FSMO Role
- Create Forest Trust
Note that you can raise the Domain functional level using AD Users and Computers while you use AD Domains and Trusts to raise Forest functional level.
AD Module for Windows PowerShell
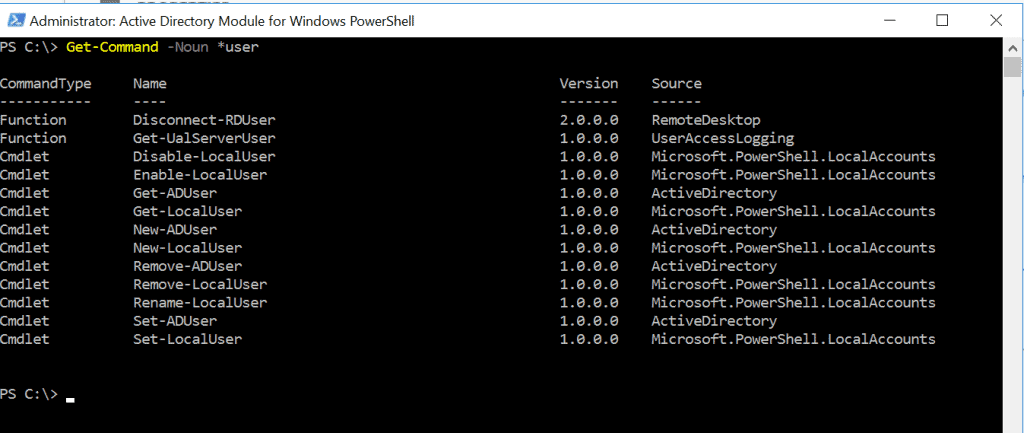
Active Directory PowerShell Module is required to manage AD with PowerShell. You can perform a number of tasks. I have listed a few below:
- Create new users – New-ADUser
- Modify existing users – Set-ADUser
- Get information about existing users – Get-ADUser
- Delete existing users – Remove-ADUser
To get all AD commands in PS, from your DC, run the Get-Command command. For more on PowerShell, read the following tutorials
18 Powershell Commands Every Windows Admin Should Kn
Get-Command in PowerShell: Applications and Use
Group Policy Management Console (GPMC)
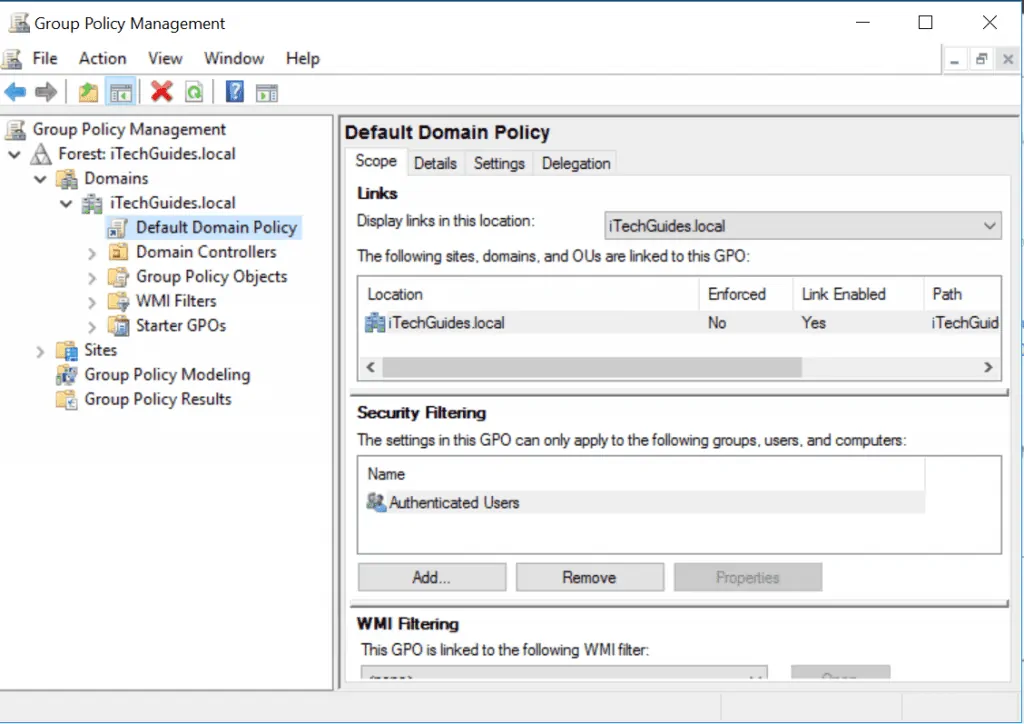
GMPC is used to manage Group Policy across sites, domains, and organizational units within one or more forests. Though you can manage Group Policies from AD Users and Computers, GPMC provides more features.
With GMPC, you can perform the following tasks:
- Create new Group Policies
- Modify existing Group Policies
- Manage all Group Policies under one container – Group Policy Objects
- Create and apply WMI filters to Group Policies.
- Create GP modelling and GP Results
Conclusion
I hope you found this article helpful. If it was helpful, kindly take two minutes to share your experience with us using the comment form at the bottom of this page.
You may also ask questions or share your experience with Active Directory. Alternatively, you can respond to the “Was this page helpful?” question below.



