This article answers the question – What is Active Directory and 49 other most widely asked AD questions.
General Questions about Active Directory
Question 1 of 50: What is Active Directory?
AD is a Microsoft Directory service that provides a method of storing objects like users and computers. AD also makes it easy for the stored information to be accessed and managed by network users and administrators.
Question 2 of 50: What is the difference Between Active Directory and Domain Controller?
As defined earlier, AD is the Directory service that manages objects. On the other hand, a Domain Controller (DC) is the Windows server running AD Domain Services (AD DS).
To make it clearer, AD is a concept while DC is a physical Windows server with AD DS installed via Server Manager.
Question 3 of 50: What is the Purpose of a Domain Controller in Active Directory?
A DC has multiple responsibilities in an Active Directory Domain. Below are some of the functions of a DC:
- Manages authentication (logon to the Domain) and authorization (access to resources)
- A DC manages Replication and Trust relationships between Domains that are connected.
- Hosts the Global Catalog server role
- A DC could also hold the 5 FSMO roles. The FSMO roles are listed and explained later in this article.
- Could be configured as a Universal Group Membership Caching (UGMC) Server.
Question 4 of 50: What is a Domain Controller Certificate Used for?
A DC certificate is required for smart card authentication. If a Domain uses smart card logon, a DC certificate is a requirement.
Question 5 of 50: What is Active Directory Authentication?
AD uses the Kerberos authentication protocol to securely allow any user access to any domain in a forest. The process of verifying the identity of a user or host is called AD authentication.
Question 6 of 50: Does AD Use LDAP or Kerberos?
AD uses Kerberos for authentication and uses LDAP for directory look-ups. In other words, LDAP is a protocol you can use to “talk” to AD while Kerberos grants users logon access to AD.
Question 7 of 50: How do Kerberos and LDAP Work Together?
This question is very similar to the previous one but this time, the question is about how Kerberos works with LDAP.
While Kerberos authenticates users, LDAP holds data about what the users are allowed to access (authorization information). What this means is that Kerberos depends on LDAP to fulfill its authorization function.
Question 8 of 50: How Does Kerberos Work in Active Directory?
So far, in this article you have read about Kerberos. By now you should know that Kerberos is the service used to authenticate users in Active Directory. What you don’t know yet is how Kerberos authentication works.
Below is the high-level steps for Kerberos authentication:
- Step 1: The authenticating client requests a Ticket Granting Ticket (TGT) from the Key Distribution Center (KDC). This is called sending an Authentication Service Request Kerberos message to the DC. The request is encrypted.
- Step 2: When the request is received by the KDC, it decrypts the request. It also performs additional verification like checking that the timestamp is within the acceptable 5-minutes interval. The KDC then sends back an encrypted TGT and session key. The returned TGC received by the client contains all the information required to access services within the Active Directory Domain.
- Step 3: The TGT is encrypted using the Ticket Granting Service (TGS) secret key
- Step 4: The client stores the TGT and can use it to access services for up to 10 hours. However, when the TGT expires the local session manager (on the client) requests a new TGT.
How the TGT is used to access services –
- Step 5: To access a service (resource like printer, files, folders, etc), the client requesting access to the service sends its current TGT to the KDC. The Ticket Granting Ticket sent by the client also includes the Service Principal Name (SPN) of the service of the resource the client wishes to access.
- Step 6: When the KDC receives the request it verifies that the user has access to the requested service.
- Step 7: Once the KDC verifies that the user or host has a valid ticket, it sends session key for the service requested to the client.
- Step 8: The final stage of the kerberos authentication process is for the client to forward the session key to the service. The session key proves that the user or host has access to the service. The service then grants access to the client.
Questions about Active Directory Features
Question 9 of 50: What is the Difference Between LDAP and Active Directory?
Active Directory is Microsoft’s implementation of a Directory service that stores information about objects. On the other hand, LDAP is a protocol that provides a means of querying AD.
Question 10 of 50: What is the Difference Between a Domain and a Workgroup?
To demonstrate the difference between a Domain and a Workgroup, I will list the features of each.
- In a Workgroup, all computers are peers. No computer controls access or logon to another computer. On the other hand, in a Domain, one or more computer serve as Domain Controllers (for a windows network). The DC controls access, security and authentication.
- Resources in a Workgroup are managed on individual computers but centralized in a Domain. For example, if you wish to access a shared folder in a Workgroup you need to have the username and password of the local computer. Sharing resources in a Domain is easier – users are granted access from the DC.
- In a Domain environment, you can log on to any computer in the Domain. Whereas in a Workgroup, you have access to individual computers.
- In a Workgroup, administrators cannot lockdown computers or users profiles using Group Policies. However, in a Domain, network administrators can control the level of access users have on computers.
- A Workgroup can have about 20 computers while a Domain can have thousands of computers
- In a Workgroup all computers must be in the same network subnet
Question 11 of 50: What is Active Directory Domain Services (AD DS)?
Active Directory Domain Services is a service that runs on a Domain Controller (DC). AD DS becomes available when a Windows server is promoted to a DC.
Question 12 of 50: What is the Purpose of Active Directory Domain Services?
A server running AD DS is called a Domain Controller. So we can say that the purpose of AD DS is to authenticate users. Also, within an Active Directory Domain, AD DS also authorizes access to resources.
Question 13 of 50: What is Active Directory Federation Services (AD FS)?
AD FS is a Windows server service that provides authentication and authorization. AD FS provides users Single Sign-on access to internet-facing enterprise applications.
Active Directory Federation Service authenticates via a proxy service hosted between Active Directory and the target application.
To read more about AD FS, click What is ADFS?
Questions about AD Installation
Question 14 of 50: How Do I install AD?
There are two ways you can install AD. One, via Server Manager. To install AD from Server Manager:
- Open Server Manager Dashboard, then click on Add roles and features.
- Select Role-based or feature-based installation and click Next.
- Select the server you want to install AD DS on – to select the servery highlight it then click Next.
- Check the box beside Active Directory Domain Services and then click Next.
- Ensure that Include Management Tools (If applicable) is checked then click Add Features. Click Next.
- On the AD DS window, click Next.
- On the confirmation window, review your selections then click Install.
AD DS installation will start. When it completes you will need to promote the server to a Domain Controller.
- Click the yellow amber warning triangle on top right of Server Manager Dashboard. Then click Promote this Server to a Domain Controller.
- Next, on the Deployment Configuration window, select the last option (Add a new Forest). Specify the Fully Qualified Domain Name (FQDN) of the Forest root domain. FQDN is in the format DomainName.<extension>. For example ITECHGUIDES.local. Click Next.
- On the next page, type in the Domain Admin password then confirm the password and click Next.
If you are deploying AD DS in a production environment, I strongly recommend installing and configuring DNS before installing AD DS. I DO NOT recommend installing DNS while promoting a server to a DC.
- Next, on the NDS Options page, click Next.
- Next, on the Additional Options page, click Next.
- On the Paths page, click Next.
- On the Review Options page click Next. Then on the Prerequisites Check page click Install.
The promotion process will begin. The server will reboot during this process.
An alternative option to install AD DS on a server is to use a PowerShell Command. To install AD DS, run the following command:
Add-WindowsFeature -name ad-domain-services –IncludeManagementTools –Restart
After installing AD DS, you need to promote the server to a DC by running the command below:
Install-ADDSDomainController -InstallDns -Credential (Get-Credential "DomainName\Administrator") -DomainName "ITECHGUIDES.local"
For a detailed step-by-step guide with images click Active Directory Domain Services: Installation & Configuration.
Question 15 of 50: Can You Install Active Directory ion Windows 10?
No. You can only install Remote Server Administration Tools (RSAT) on Windows 10. AD DS can only be installed on a Windows Server.
Question 16 of 50: How do I Run RSAT in Windows 10?
Follow the steps below to install RSAT in Windows 10:
- Step 1: Download RSAT for Windows 10 by clicking this link Remote Server Administration Tools for Windows 10.(Opens in a new window).
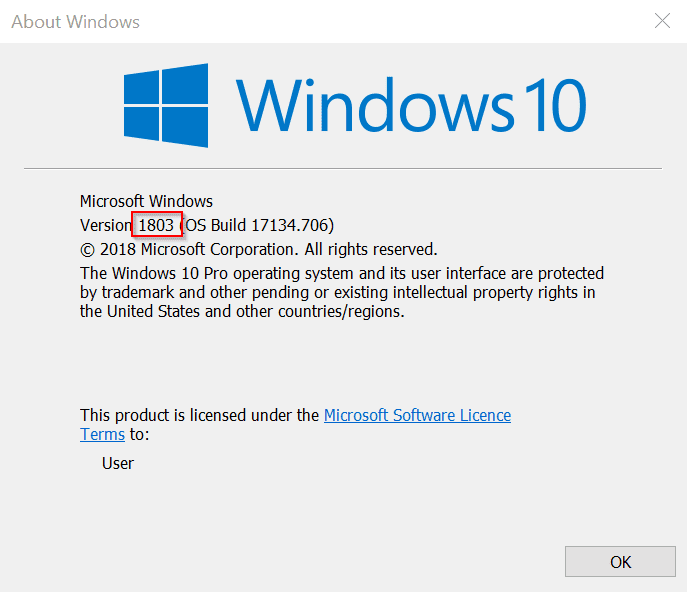
Ensure you download the right RSAT for your OS build and processor architecture. To determine your Windows 10 build execute the command below in cmd:
winver
This will open information about your OS build. See the first image below.
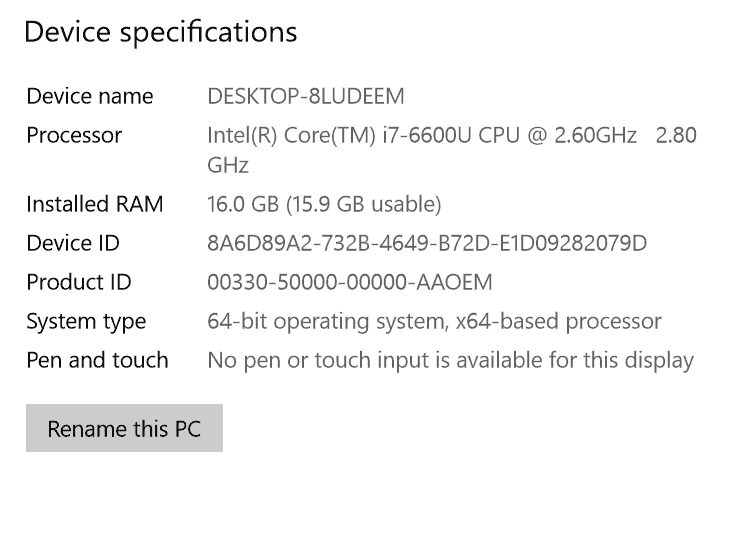
Next, you need to determine your OS architecture – whether you are running x64 or x86. To do this right-click the Windows logo on your task bar and click System. Look beneath Device Specification, System Type. See the second image below.
Finally, with these information determine the RSAT version you need to download. The third image has available RSAT versions as at the time of writing this tutorial.
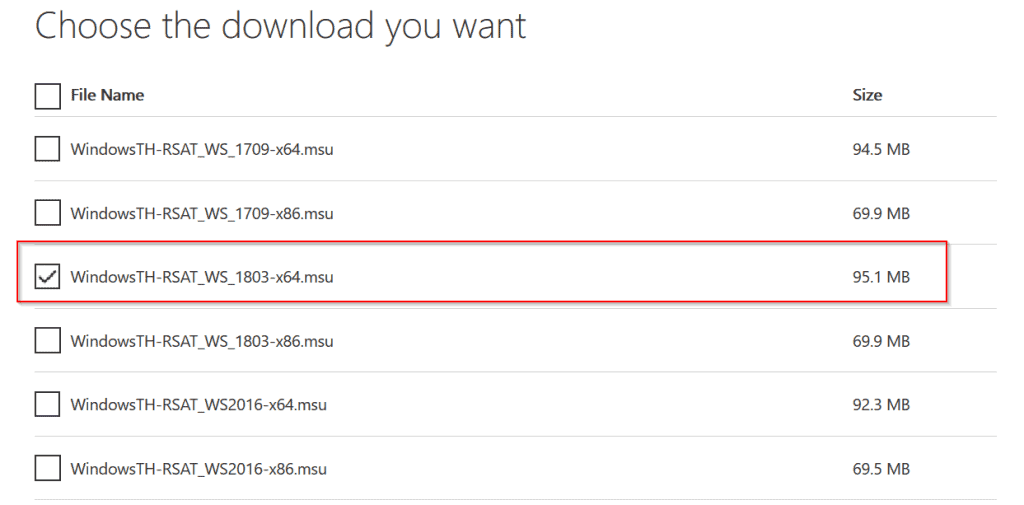
Download the correct version of RSAT for your OS build and save the file on your computer.
- Step 2: Install RSAT by double-clicking the file then click Yes to the Windows Update Standalone Installer. Then when prompted, accept the license agreement.
- Step 3: When the installation completes RSAT becomes available. As an example you can now access Active Directory Users and Computers.
Congratulations! You have successfully installed RSAT for Windows 10.
Question 17 of 50: How do I Enable Active Directory Users and Computers in Windows 10?
By installing Remote Server Administration Tools (RSAT). See the previous question to see how to install RSAT.
Questions about Active Directory Infrastructure
The questions covered in this section range from Active Directory Logical and Physical structure to FSMO roles and more.
Question 18 of 50: What is the Active Directory Structure
Active Directory structure is broken down into 2 parts – Logical and Physical structure. These structures are driven by objects, organizational units, domains, trees, and forests.
For a detailed look at the logical and physical structures of Active Directory, see Question 22 of 50 later in this tutorial.
Question 19 of 50: What is a Forest in Active Directory?
An Active Directory Forest is a collection of Domain Trees that do not share a common parent domain name.
For instance, say a fictitious company, Company A acquires another company, Company B. After the acquisition the AD domains of the two companies will need to share resources.
To get the two domains to communicate you create a forest relationship. The moment you create that relationship you have created an AD Forest.
Question 20 of 50: What is an Active Directory Domain?
Domain is is the basic structure of Active Directory. A Domain interconnects objects in in an Active Directory network.
An AD object could be a user, computer or printers. The structure that interconnects these objects is called a Domain.
Question 21 of 50 What is OU in Active Directory?
An OU or Organizational Unit is an AD container used to group objects. One benefit of creating OUs is to make administration easy and more organized.
An OU also provides other administration benefits like ease of Group Policy application. As an example, you could create an OU containing all computers for users in the accounting department. Because all the computers are used by staff in the same department they are likely to have the same requirements. You could apply group policies to all computers in the OU.
Question 22 of 50: What is Logical and Physical Structure of Active Directory?
The physical structure of AD are Domain Controllers and Sites.
On the other hand, the “Logical structure” of AD are components that are virtual. The components that make up the logical structure of AD are: forests, trees, domains, OUs and global catalogs.
Question 23 of 50: What is Tree in Active Directory?
A Tree is a collection of Active Directory Domains that share a common parent namespace. As an example CompanyA.com, Accounting.CompanyA.com, Sales.CompanyA.com form a Domain Tree because they all share a common namespace “CompanyA.com”
A combination of two ore more Domain Trees form a Forest.
Question 24 of 50: What is Universal Group Membership Catching (UGMC) in Active Directory?
In Active Directory universal groups may contain group memberships from any domain in the forest. Global Catalog servers store information about universal group memberships.
Moreover, in a multi-domain forest (with universal group memberships available), when a user logs on to the domain for the first time a Global Catalog (GC) server must be contacted to provide the users universal group membership information.
However, in small or remote sites a Global Catalog server may not be available. In this instance, universal group membership caching may be enabled on the site so DCs in the site may perform the function of the Global Catalog server.
With UGMC enabled, when a user logs on to the domain for the first time, the DC with UGMC enabled contacts a GC server to pull universal group membership information. This information is then cached. For subsequent logons by the same user, the DC will process universal group membership without having to contact a GC server.
Question 25 of 50: What is the Use of Global Catalog (GC)?
A global catalog server holds a partial replica of frequently searched attributes of every object in the forest. The GC holds attributes frequently searched for across the forest.
Examples of attributes held by the Global catalog server are user’s first name, last name and logon name.
Because the GC holds attributes frequently searched for, it makes it easy for users to find objects across the forest without knowing what domain holds the objects.
Question 26 of 50: What is Active Directory Multi-master and Single-master Operations?
An Active Directory Domain usually has more than one Domain Controller DC). When objects are created or modified, they are usually made in one DC. The DC where the change is made then replicates the changes to other DCs.
Multi-master operation model means that any DC within the AD Domain can update the Active Directory database and replicate the change to every other DC. What this means is that for general AD operations all DCs are “Master”. This is called the AD multi-master model.
However, there are certain operations that cannot be handled by the multi-master model. These operations are called single-master operations. That is, one Domain Controller is designated the role or responsibility to carry out such operations.
Furthermore, the reason for the single-master (“one master”) is due to the nature of such tasks. If two DCs were to perform such operations it would lead to conflict.
In AD, the single-master operations are called Flexible Single Master Operations (FSMO). There are 5 FSMO roles. RID Master, Schema Master, Domain Naming Master, Infrastructure Master and PDS Emulator Master. To read more about the FSMO roles, read Active Directory: Concepts, Installation & Administration.
Question 27 of 50: What are the 5 AD FSMO Roles?
The 5 FSMo (Flexible Single Master Operations) roles are: RID Master, Schema Master, Domain Naming Master, Infrastructure Master and PDS Emulator Master.
Question 28 of 50: What is Active Directory RID Master?
The Domain Controller responsible for allocating RID pools to other DCs is the RID Master.
Question 29 of 50: What is Active Directory Infrastructure Master?
The DC assigned the Infrastructure Master FSMO role is responsible for updating cross-domain object references.
Question 30 of 50: What is Active Directory Domain Naming Master?
The Domain Naming Master is responsible for adding and deleting domains in the forest. It also updates cross references to domains in external directories.
Question 31 of 50: What is Active Directory PDC Emulator Master?
The DC assigned this role manages authentications and password as well as time synchronization. The PDC emulator also manages account lockouts and forwards authentication failures triggered by incorrect passwords to other DCs.
Question 32 of 50: What is Active Directory Schema Master?
The Schema master handles all AD schema updates.
To read more about FSMO roles, click Active Directory: Concepts, Installation & Administration.
Questions about Active Directory Security
The questions covered in this section are about security groups and certificates.
Question 33 of 50: What are Active Directory Security Groups?
An AD security group is an object that allows administrators to assign and manage access to resources. Instead of assigning access to individual users, best practice is to use security groups.
Below is an example of a security group.
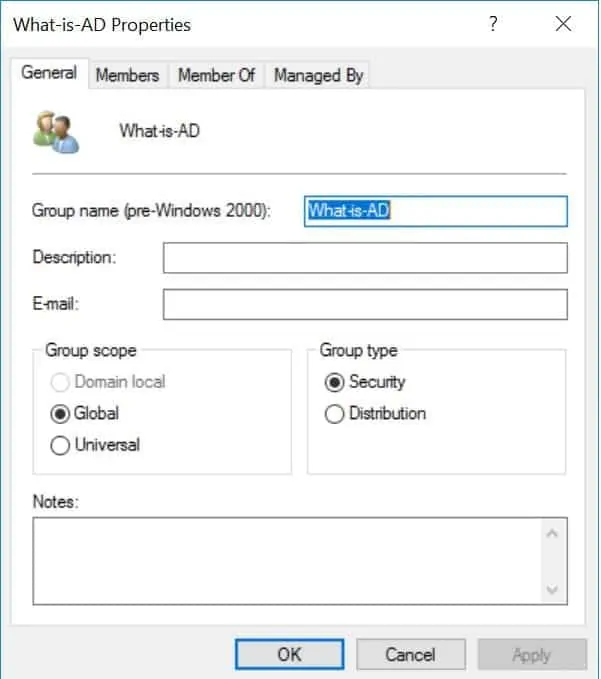
As you can see from the image above, an AD security group can be a Domain local, Global or Universal group. To read more about group types and scopes click Active Directory Security Groups.
Question 34 of 50: How Do I Publish a Certificate in Active Directory?
Before I show you how to publish a certificate, I need to show you how to add the Active Directory Certificate Services role. Here are the steps:
- Log on to a Domain Controller and open Server Manager. Then click Manage and select Add Roles and Features.
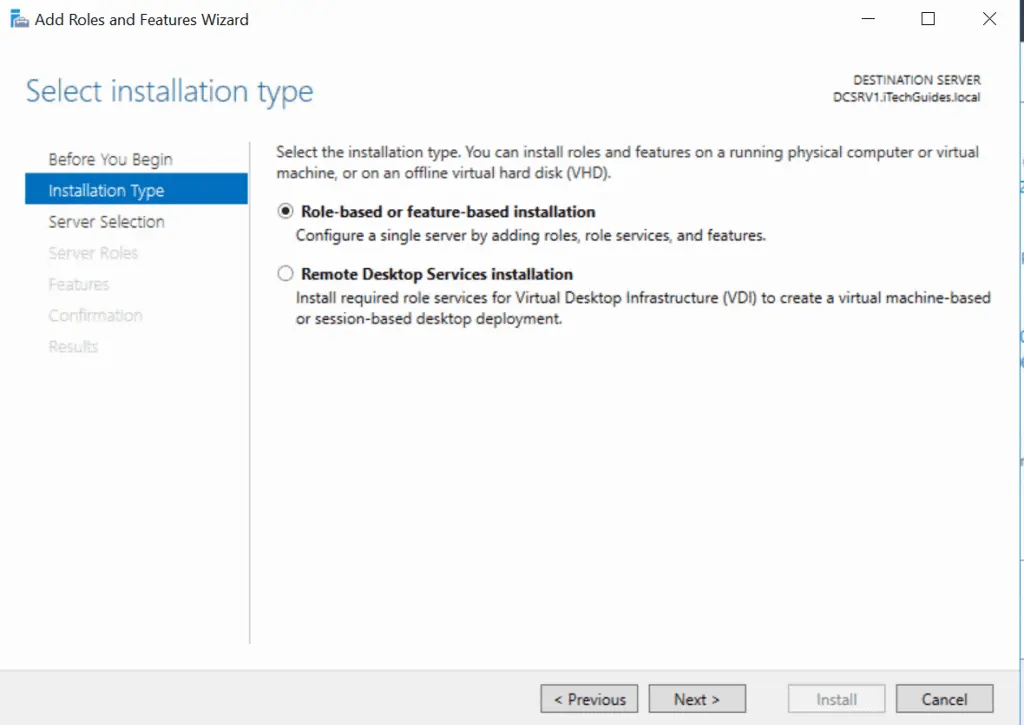
- On the Before you Begin page, click Next. Then select Role-based or Feature-based installation and click Next.
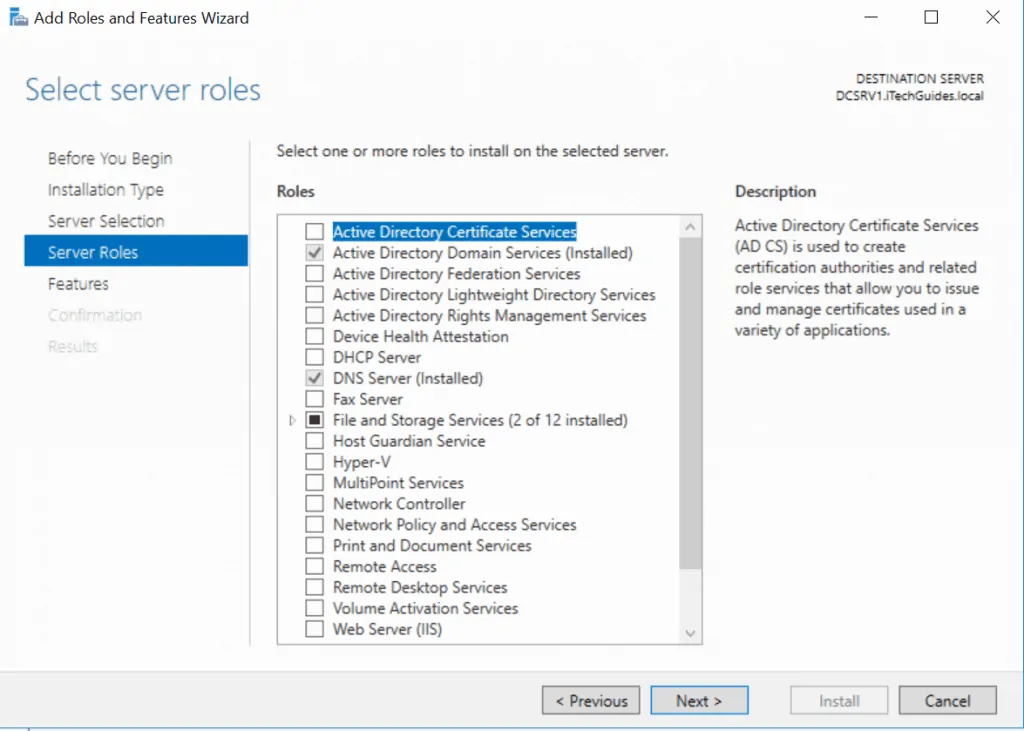
- Select the destination server then click Next. On the Select Server Role page, check the box beside Active Directory Certificate Services. Then click Add Features. To proceed click Next.
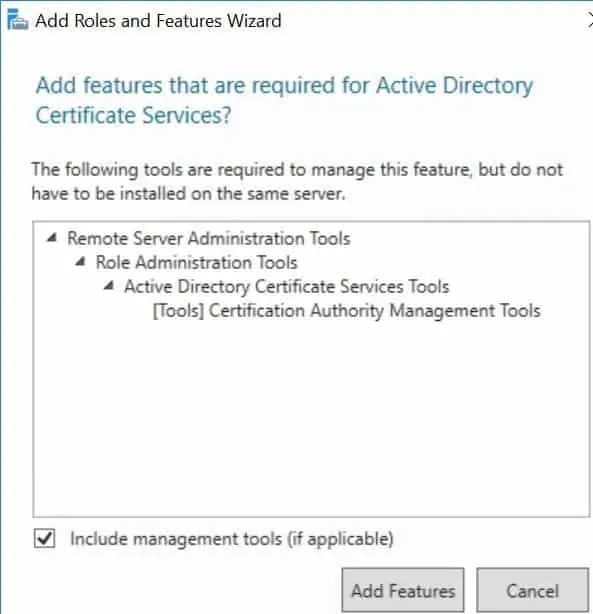
- Continue clicking Next until you get to the Confirmation page, then click Install. Give the wizard time to install the role.
Configure AD Certificate Services
- Still on Server Manager, click the yellow amber warning triangle at the top right corner of the page. Then select Configure Active Directory Certificate Services on the destination server.
- Review the information on the Credentials page, click Next.
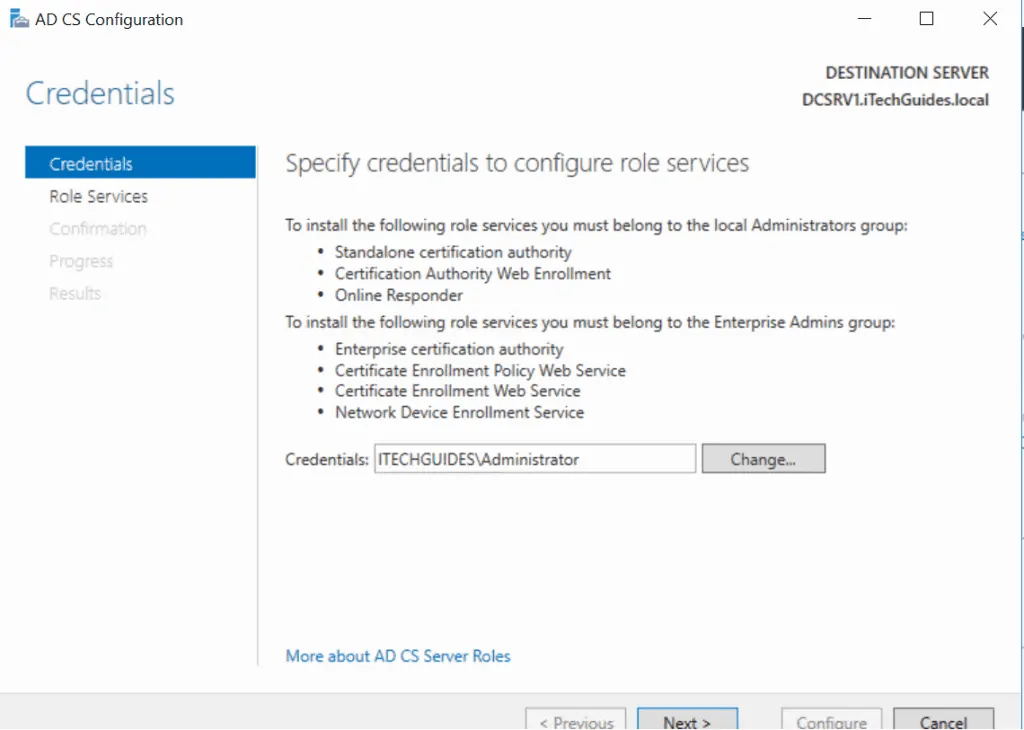
- Check the box beside Certificate Authority and click Next.
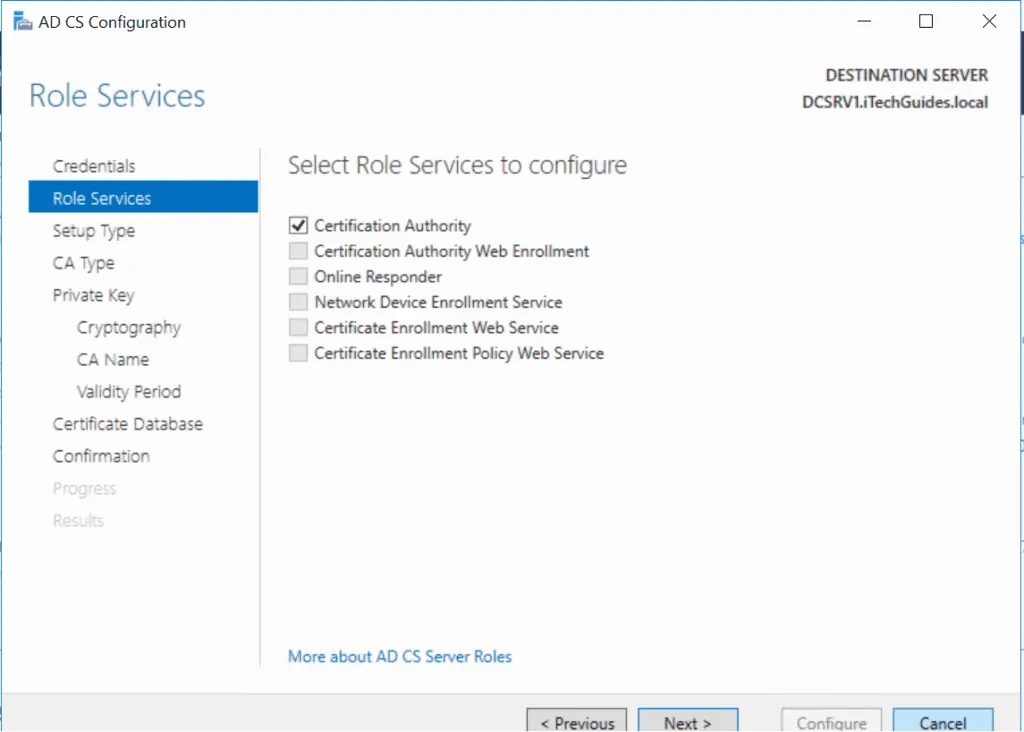
- On the Select Type page, select Enterprise CA and click Next.
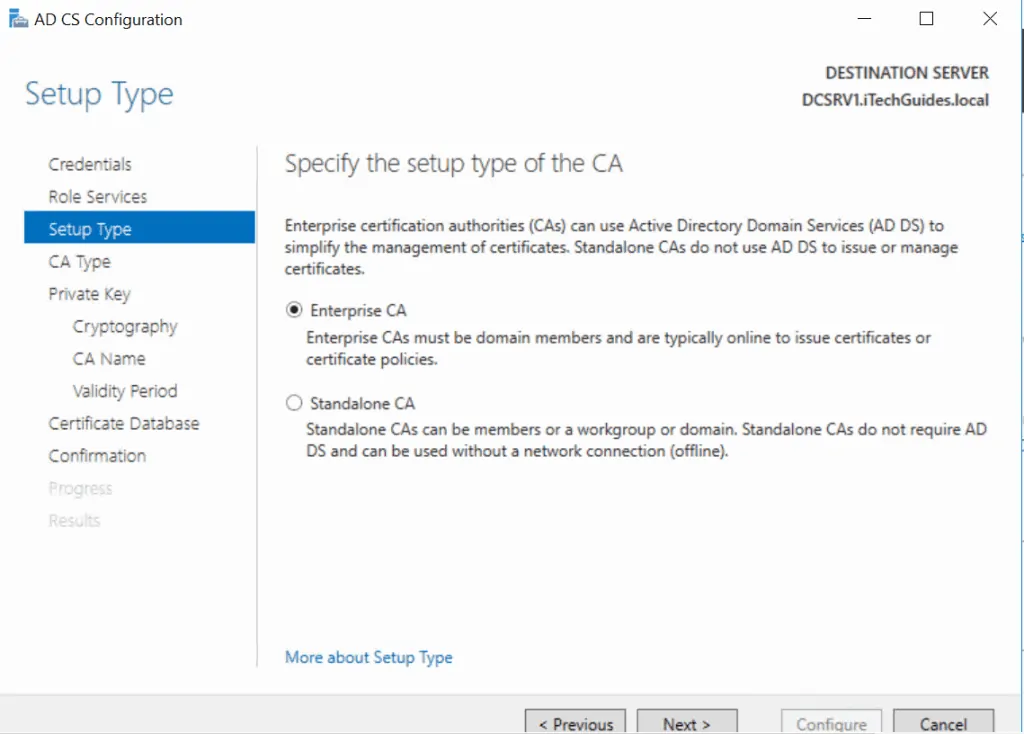
- Select your certificate type and click Next. For this tutorial, I selected Root CA.
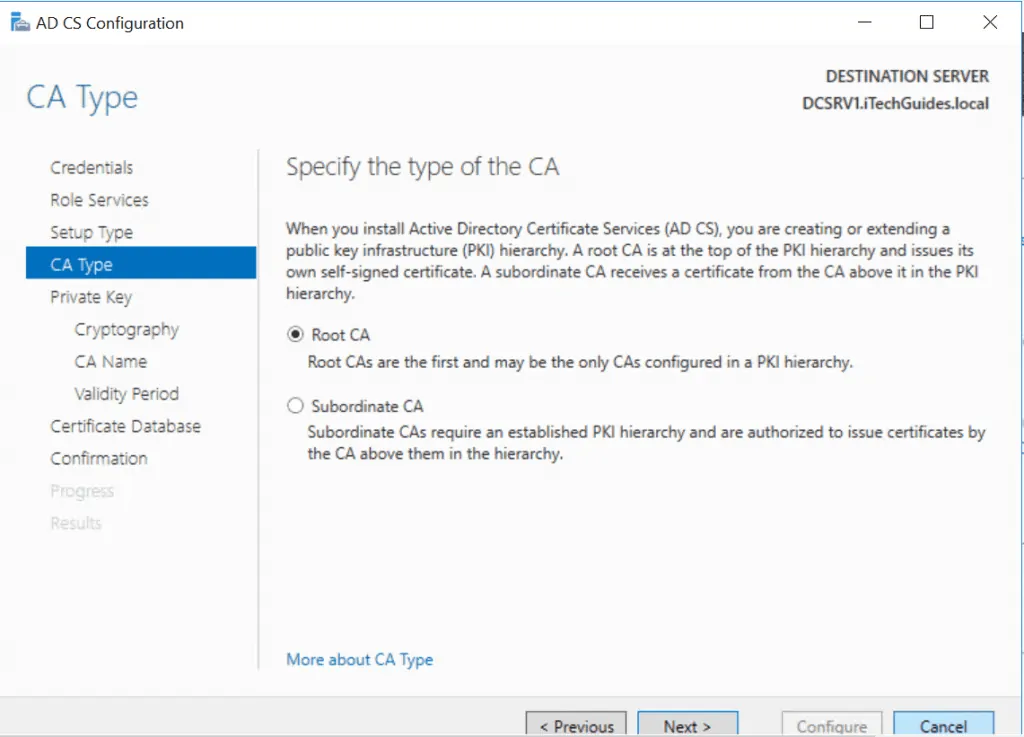
- Select to create a private key or use an existing one.
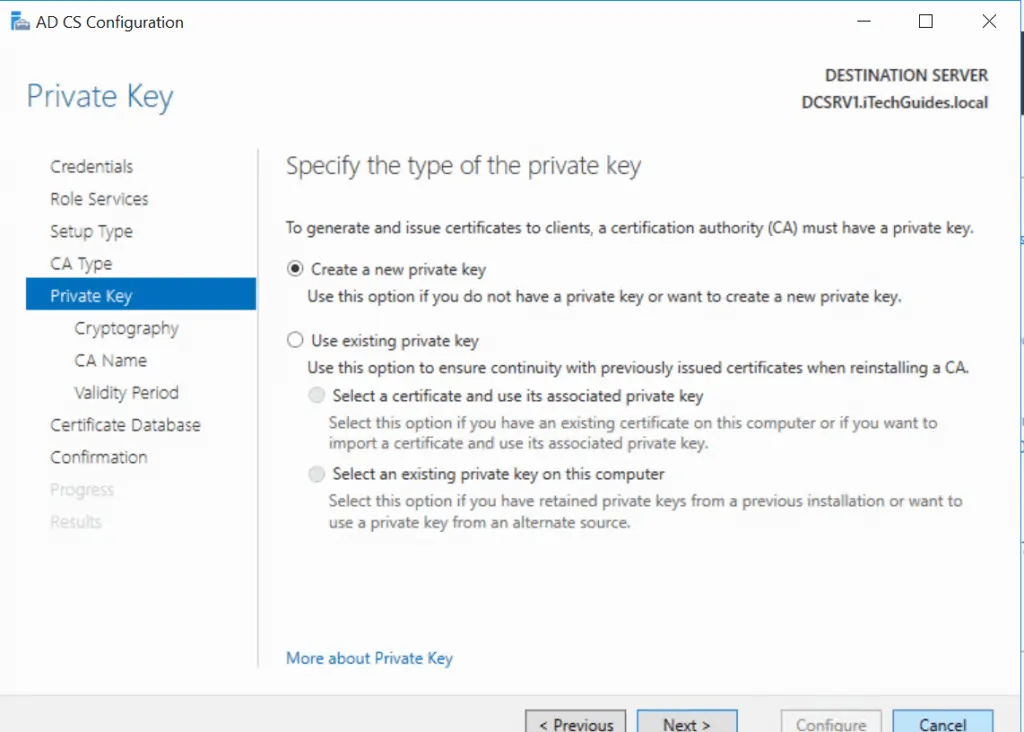
- Select a Cryptography for the CA then click Next.
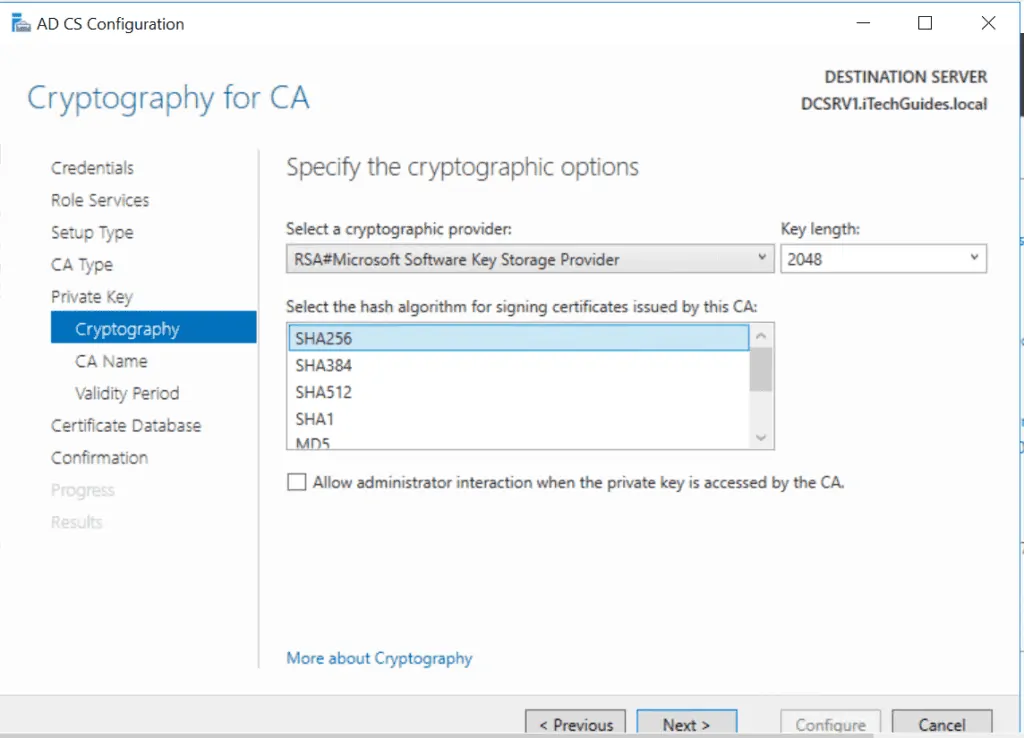
- Accept the default name for the CA offer a name.
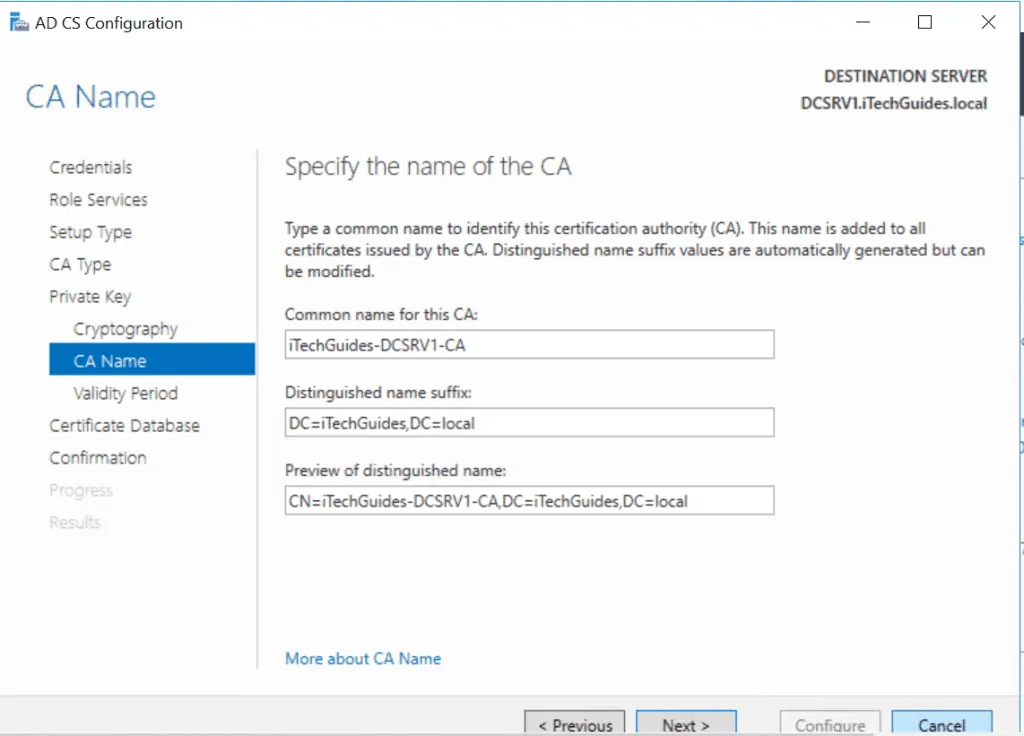
- Enter a validity period for the Certificate. Then click Next.
- Accept the default CA database path or provide a different path.
- Finally, review your selection and click Configure.
How to Issue or Publish a Certificate
- Still on Server Manager, click Tools then select Certificate Authority. The CA MMC opens.
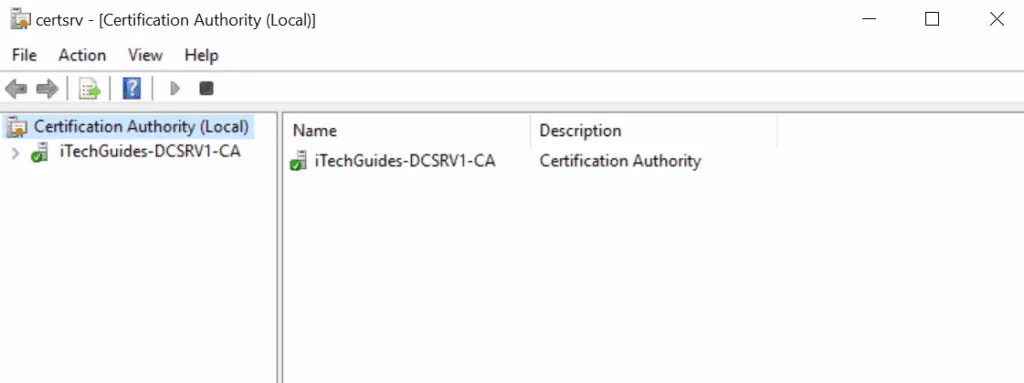
- Click the arrow beside the name of your certificate. Right-click Certificate Templates, point to New and click Certificate Template to Issue.
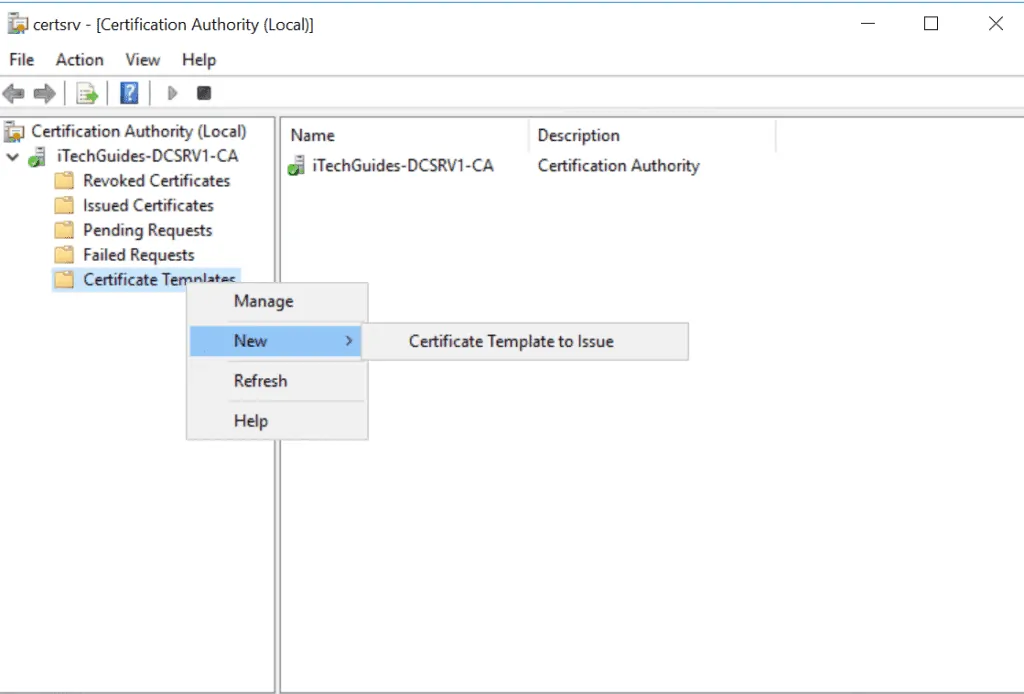
- Select a certificate template then click Ok.
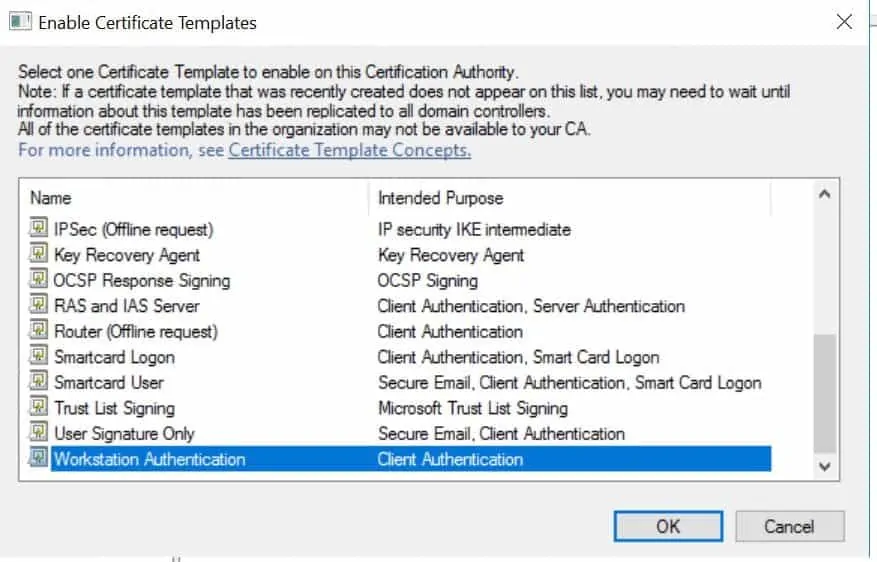
You can complete the above tasks using Windows PowerShell commands. To install a AD Certificate role, run the command below:
Add-WindowsFeature Adcs-Cert-Authority -IncludeManagementTools
After AD CS is installed, execute the following command to configure it .
Install-AdcsCertificationAuthority -CAType EnterpriseRootCA
Question 35 of 50: Does Certificate Authority Have to be on Domain Controller?
No. However, the CA MUST meet the following requirements:
- The server must be configured with a static IP address and
- It must be joined to the domain
Questions about AD Maintenance
This section covers questions about Active Directory backup and restore, Sysvol, Ntdsutil and more.
Question 36 of 50: How Do I Use Directory Services Restore Mode (DSRM)?
In Windows Server 2016, this is now called Directory Services REPAIR Mode
DSRM is a safe mode that allows administrators to recover a corrupt OS or AD Database. To use Directory Services Restore Mode, follow the steps below:
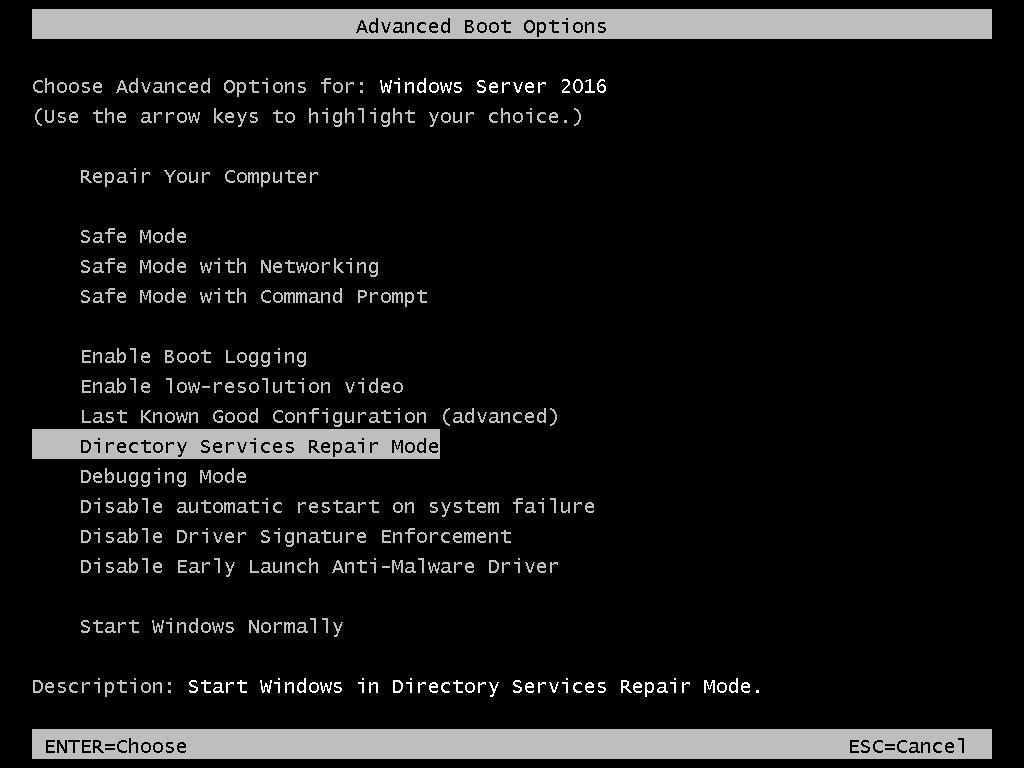
- Restart the Domain Controller – just when it reboots (post BIOS) press F8 several times. The server will load Advanced boot options.
- Use the arrow keys to select Directory Services Repair Mode then press the ENTER key to continue. The server will boot as normal.
The only difference is that the edges of the server will have “Safe mode”. With the server booted to DSRM you can perform tasks that you will not normally be able to perform in full boot mode.
Below are some of the tasks you can perform when a DC is booted to Directory Services Repair Mode:
- Perform Authoritative and non-Authoritative AD restore
- AD System State restore
- Relocate AD Database and log file
- Perform offline De-fragmentation of AD Database
- Fix DC boot issues.
When you complete your task, reboot the server to normal boot mode.
Question 37 of 50: How Does Active Directory Authoritative Restore Work?
Authoritative AD restore means that the restored data is not over-written via replication. The restored data is marked as Authoritative. That is, the DC where the Authoritative restore is performed forces other DCs to replicate the restored data.
On the other hand, a non-Authoritative restore allows update from other DCs via replication.
To perform an authoritative or non-authoritative restore you must boot the server into Directory Services Repair Mode (DSRM). See Question 36 of 50 for more information.
Question 38 of 50: What is System State Restore?
System state restore restores all the files required to recover AD DS. System state backup includes at least the following data, plus additional data, depending on the server roles that are installed:
- Registry
- COM+ Class Registration database
- Boot files
- SYSVOL directory
- Active Directory database (Ntds.dit) file and log files
- System files under Windows Resource Protection
- Active Directory Certificate Services (AD CS) database
- Cluster service information
- Microsoft Internet Information Services (IIS) metadirectory
Question 39 of 50: How do I Backup Active Directory Users and Computers?
You cannot backup Active Directory Users and Computers. However, you can backup Active Directory by backing up the server’s system state data. You can backup Active Directory using one of two tools: Windows Server Backup or Wbadmin.exe.
Before you can use Windows Server Backup you have to install the feature using Server Manager.
Once you have installed the feature, follow the steps below to complete an AD (system state) backup.
- From Server Manager, click Tools then select Windows Server Backup.
- On the Windows Server Backup, click Backup Once..
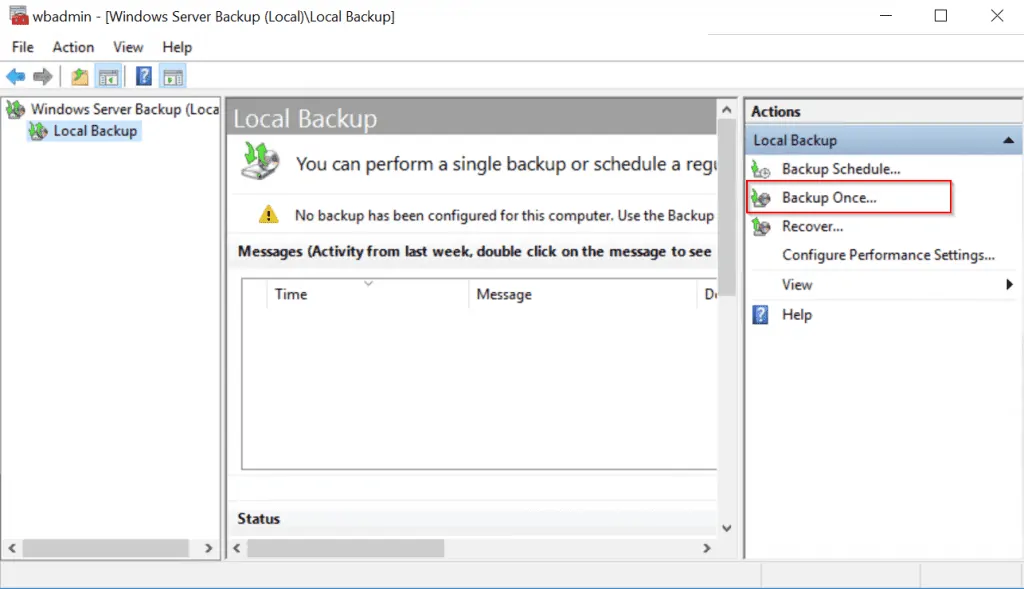
- The Backup Once Wizard opens. Click Next.

- On the Select Backup Configuration page, select Custom. Then Click Next.

- Click Add items. Then on the window that pops up, check system state and click Ok. – see the second image below.

- Back on the Select items for Backup page, click Next
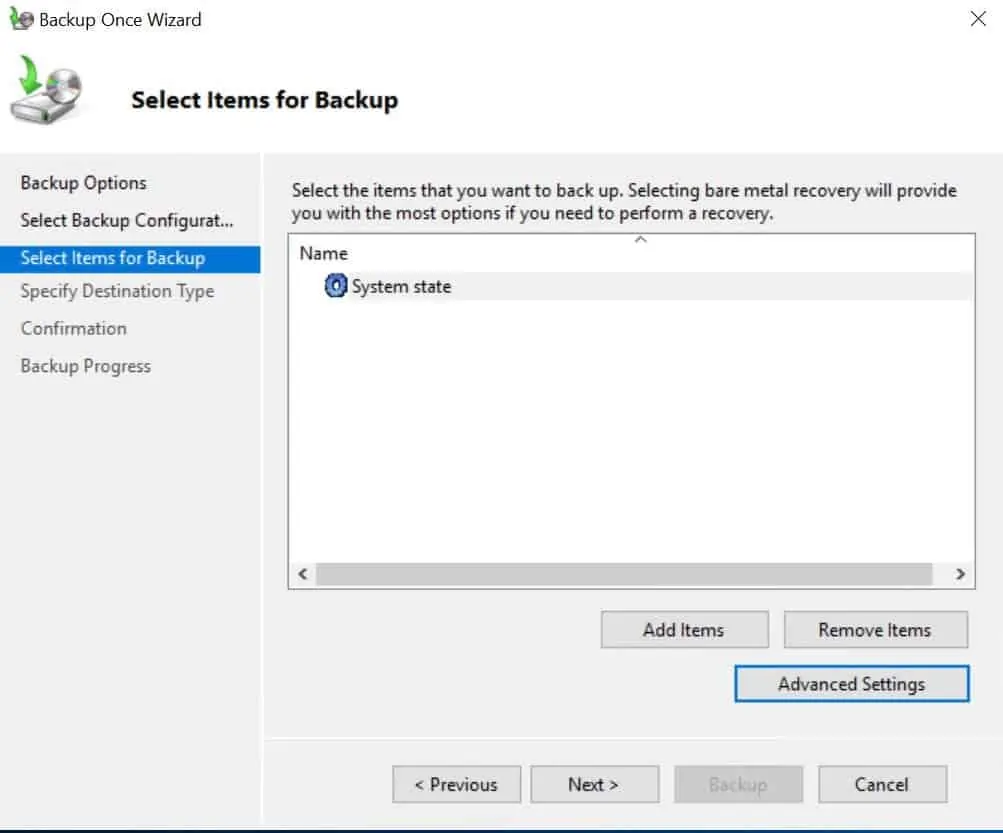
- Select Backup location. If you do not have a drive other than drive C, select Remote shared folder. Then click Next.
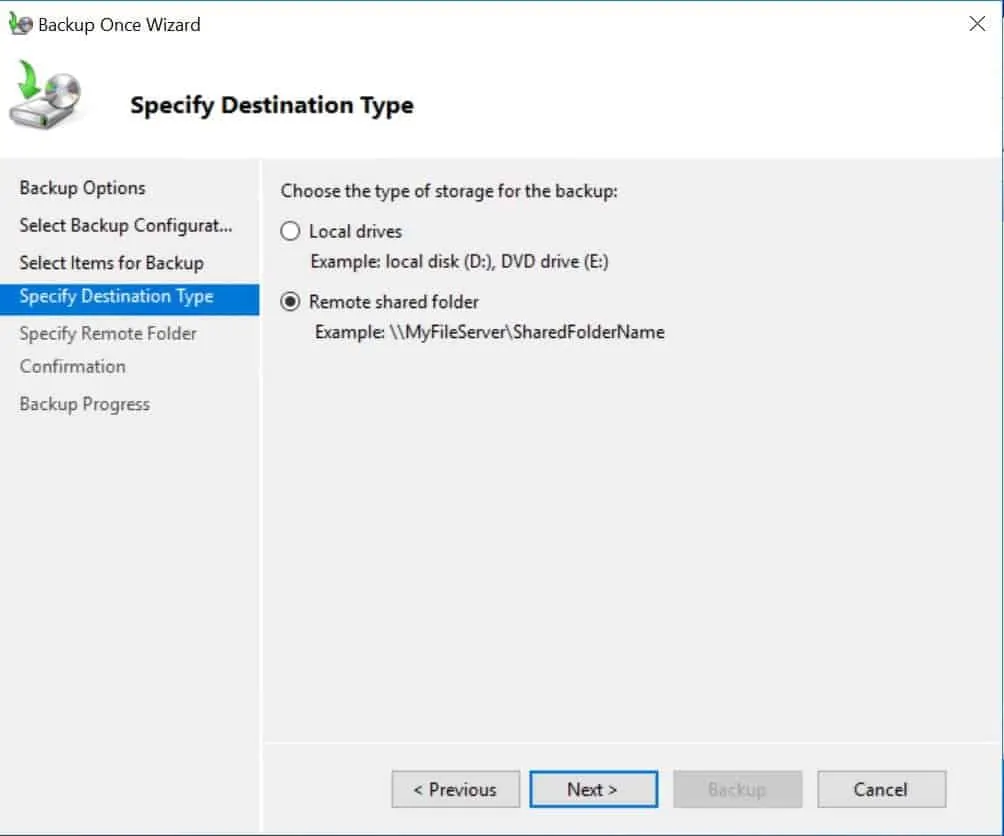
- Specify the remote shared folder path then click Next.
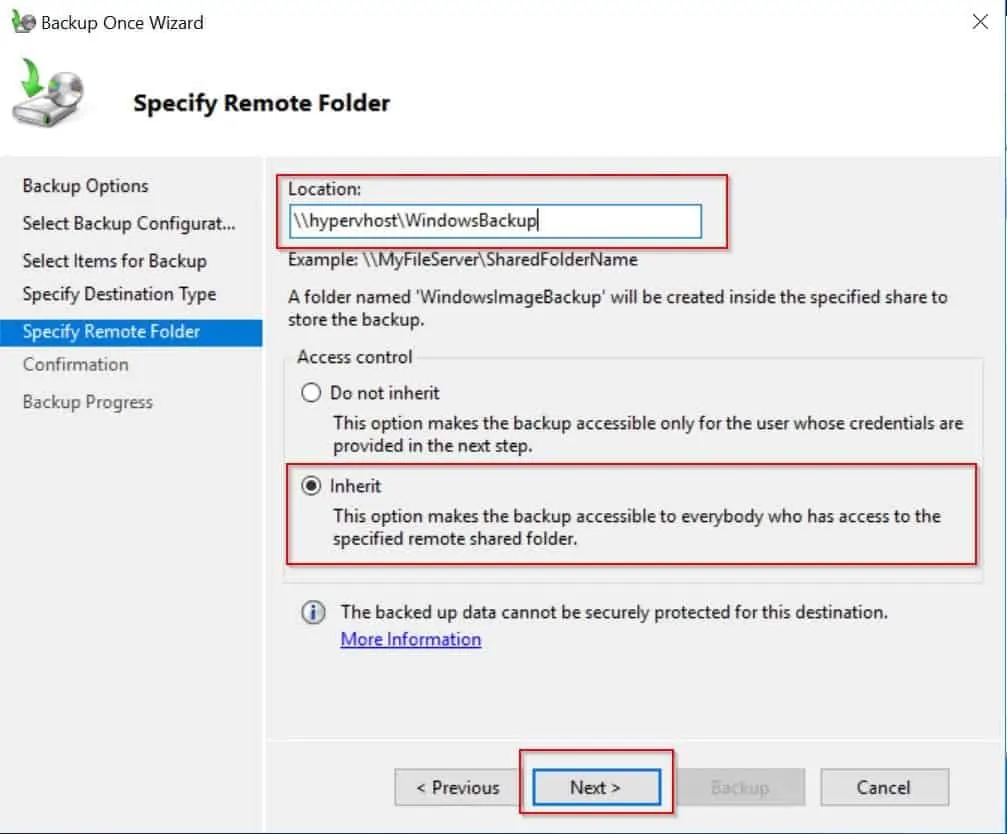
- Finally, on the Confirmation page, click Backup. Then wait for the backup to complete.

Question 40 of 50: What is SYSVOL?
SYSVOL is a folder in a Domain Controller where GPOs and scripts are stored. Two folders exist in this location – %WINDIR%\SYSVOL\domain – Policies and Scripts.
Group Policies are saved in %WINDIR%\SYSVOL\domain\Policies. Logon scripts or other files are saved in %WINDIR%\SYSVOL\domain\Scripts. The Scripts folder is shared as NETLOGON.
If SYSVOL replication to a particular DC stops, the DC will no longer be up to date. The Domain Controller with PDC Emulator operation master role will always have updated copy of the SYSVOL. So it is the best place to look for the updated copy.
Any other DC that is out of sync will have to be updated using Non-Authoritative SYSVOL restore.
Question 41 of 50: What is Ntdsutil Command Used for?
NTDSUTIL, a command line tool is used to perform the following tasks:
- Perform Offline Defragmentation of Active Directory Database
- Relocate AD Database and log files
- Create Active Directory snapshots
- Perform metadata cleanup
Question 42 of 50: How do I Restore My AD?
The answer to this question depends on the type of Active Directory restore you wish to perform. For most AD restores, you will need to boot your DC to Directory Services Repair Mode (DSRM) then perform your restore.
If you need help booting your Domain Controller to DSRM see Question 36 of 50 (opens in a new window). In most cases, restoring system state will restore AD.
Questions about AD Tools
Questions in this section covers AD Users and Computers, Sites and Services, Replication and more.
Question 43 of 50: What is Active Directory Users and Computers?
This is one of the most used AD tools. It is used to create new users or modify existing users. It is also used to create and Organizational Units (OUs). Wit AD Users and Computers you can also raise the Domain Functional levels and more.
Question 44 of 50: What is Active Directory Sites and Services?
This is the primary tool used to configure and manage AD replication. You can also complete the following tasks using this tool: Enable Universal Group Membership Caching (UGMC), Inter-Site Transports and Subnets.
Question 45 of 50: What is Active Directory Domains and Trusts?
This AD tool is used primarily to create forest trusts. It can also be used to raise Forest functional level and transfer Domain Naming Master role.
Question 46 of 50: What is the Only OU Created by Default After Installing Active Directory?
Domain Controllers OU.
Question 47 of 50: What is Active Directory Replication?
AD Replication is a process Domain Controllers use to update data with each other. Replication topology defines the interconnection between DCs that participate in replication.
Question 48 of 50: What is KCC in Active Directory?
Following up from the answer to the previous question, KCC (Knowledge Consistency Checker) designs the replication topology automatically. In other words KCC generates the replication topology between Domain Controllers.
Question 49 of 50: What is Inter-Site Transports?
Inter-site transport is a container in Active Directory Sites and Services. It is used to create and store site links. It has two sub-containers – IP and SMTP. You can create 2 types of site links – IP or SMTP.

A site link is a connection between sites
If you create a site link in the IP container, the link will use the Internet Protocol (IP) as its transport protocol. On the other hand, site links created in the SMTP container will use Simple Mail Transfer Protocol (SMTP).
Question 50 of 50: How Many Types of Replication Are There in Active Directory?
On the other hand, intra-site replication happens between DCs in two different sites.
Conclusion
Here you have them. 50 Active Directory questions answered.
Kindly share your feedback about this guide using the comments form at the bottom of this page. You may also ask questions.



