Combing NTFS permissions with share Permissions increases folder security within a network. Every Windows Administrator should have a detailed understanding of the two types of permissions and how to use them effectively.
What are NTFS Permissions and Share Permissions?
NTFS Permissions are used to control access to files and folders on a local computer and over the network. NTFS permissions can only apply to files and folders on volumes formatted with NTFS file systems.
NTFS means New Technology File System. It was introduced in Microsoft’s Windows NT and have been used in subsequent Windows Operating Systems.
Share permissions control access to shared folders and only applies when a user accesses a folder over the network. This type of permission do not apply to users logged on to the local computer. Share permissions applies to folders in volumes formatted with both NTFS, FAT and FAT32 file systems.
In this tutorial you will learn:
- Features of NTFS Permissions
- Features of Shared folder Permissions
- NTFS Permissions vs Share Permissions: How they Interact
- Configure NTFS and Share Permissions
- How to Configure NTFS Permission Inheritance
Features of NTFS Permissions
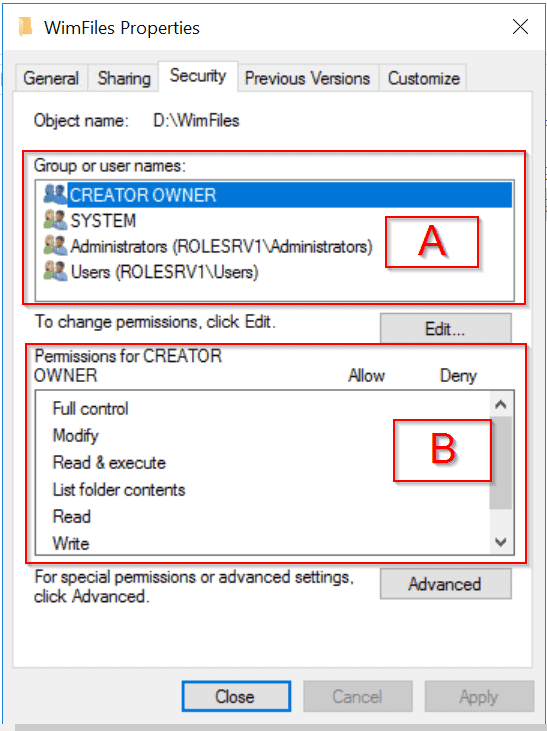
NTSF permissions are controlled via the Security tab of the folder’s properties settings. Refer to the image above. The part labelled “A” lists users that have access to the folder. Part “B” lists the permissions these users have.
Available NTFS Permissions
As shown in the previous image, a user can be granted 6 permissions. I have described each below
“Full Control” Permissions
Grants the user ability to crate, modify or delete files and subfolders within the folder. Full Control permission also enables the user to traverse folders and execute programs in the folder. Finally, this also grants the user ability to modify the permissions for the folder and all subfolders and files
“Modify” Permissions
A user granted the “Modify” NTFS permission will be able to create and delete folders. The user can also modify the properties of the folder.
“Read & execute” Permissions
This permission grants a user the right to view files and folders. The user is also able to run executable files, including scripts.
“List folder contents” Permissions
“List folder contents” permission grants the user the ability to view and list the contents of a folder. The user can also execute files and view the folder’s attributes.
“Read” Permissions
Allows a user to view the contents of the folder, including files and subfolders.
“Write” NTFS Permissions
Grants the access to add new files and subfolders to the folder. A user with “Write” permission will also be able to write to a file within the folder.
Features of Share Folder Permissions
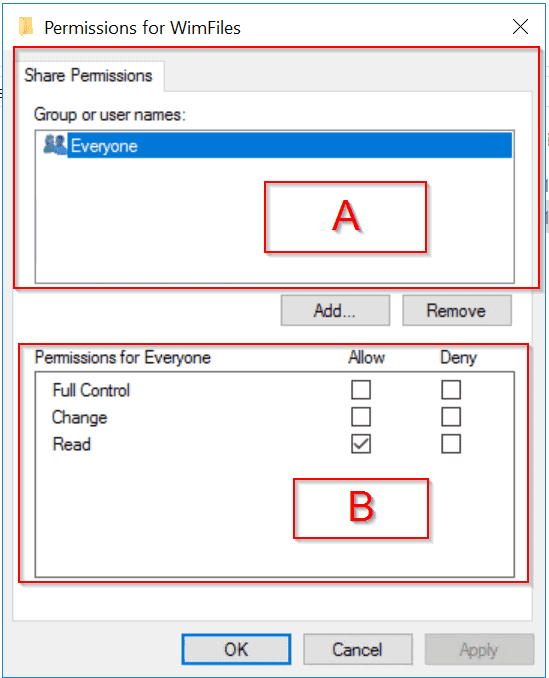
The image above shows the share permission of a folder. It is available via the Sharing tab of a folder’s Properties settings. In the image, the part labelled “A” is where you add users that require access. “B” is where you modify the permission you wish to grant or deny the users.
Later in this tutorial, I will show you how to share a folder and modify share permissions. In this section I will explore the various types of permissions you can grant a user.
Available Share Permissions
Below are the various permissions you can grant or deny a user when you share a folder.
“Read” Permissions
“Read” share permission allows a user to view the contents of a folder. By default, the “Everyone” group is assigned “Read” permissions.
“Change” Permissions
A user granted the “Change” permission has all the permissions granted by “Read”. The user can also create and delete files and subfolders in the folder.
“Full Control” Permissions
The “Full Control” share permission grants users the access granted by “Read” and “Change”. However, it also grants edit permissions and ability to take ownership of files. By default, the “Administrators” group is granted “Full Control” permissions.
NTFS and Share Permissions Synergy
One question in the minds of entry-level admins is this “When you configure NTFS permissions and Share permissions, which one takes precedence”. This section will answer that question.
The table below highlights the key features of both permissions and how they work together.
| S/N | Features | NTFS Permissions | Share Permissions |
|---|---|---|---|
| 1 | Permissions Precedence | If a folder has both NTFS permissions and share permissions, the most restrictive permission applies | |
| 2 | Application to File Systems | Can only apply to folders on volumes formatted with NTFS file system | Can apply to folders on volumes formatted with FAT, FAT32 and NTFS file systems |
| 3 | Permissions Control | Allows more granular control – like configure subfolder permission inheritance | Easy to manage but does not allow granular control |
| 4 | Concurrent connections Restrictions | NTFS permissions does not have the option to restrict the maximum allowed concurrent connections. | You can specify how many connects allowed concurrently. |
| 5 | Location of Configuration settings | Accessed via the Security tab of the folders Properties settings. | Share permissions can be configured via the Sharing tab of a folders Properties – by either using the Share or Advanced Share button |
| 6 | Application to network or local users | Applies to users logged on to the local computer. | Does not apply to users logged on to the local computer. |
Configure NTFS and Share Permissions
In this section, I will walk you through the steps to configure NTFS permissions and Share permissions. The section will conclude by walking you through NTFS Permission Inheritance configuration.
How to Configure NTFS Permissions
- Right-click the folder and click Properties.
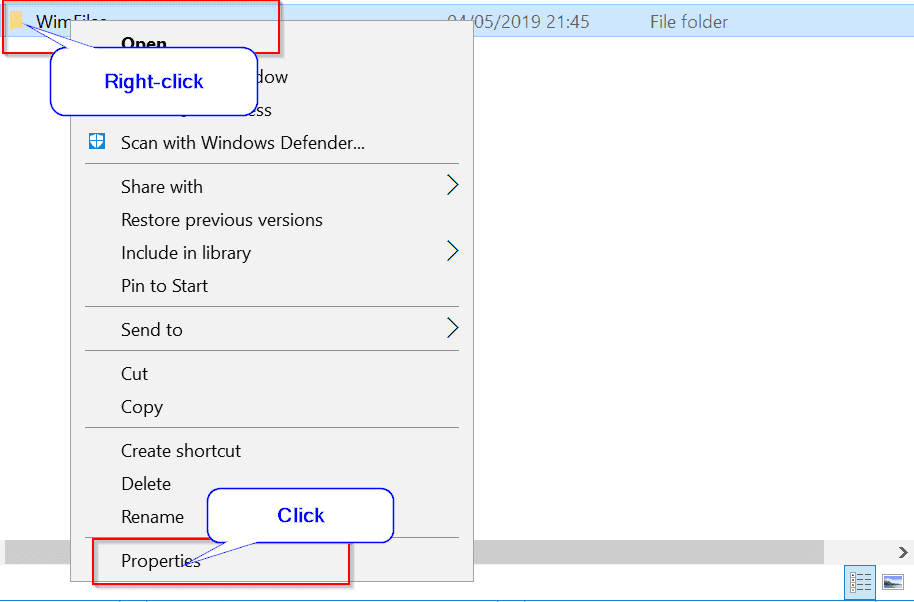
- To modify the NTFS permissions of the folder, click the Security tab.
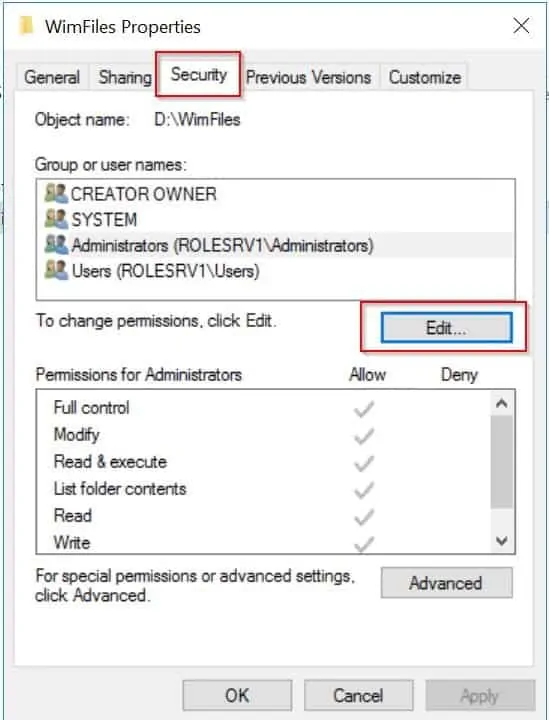
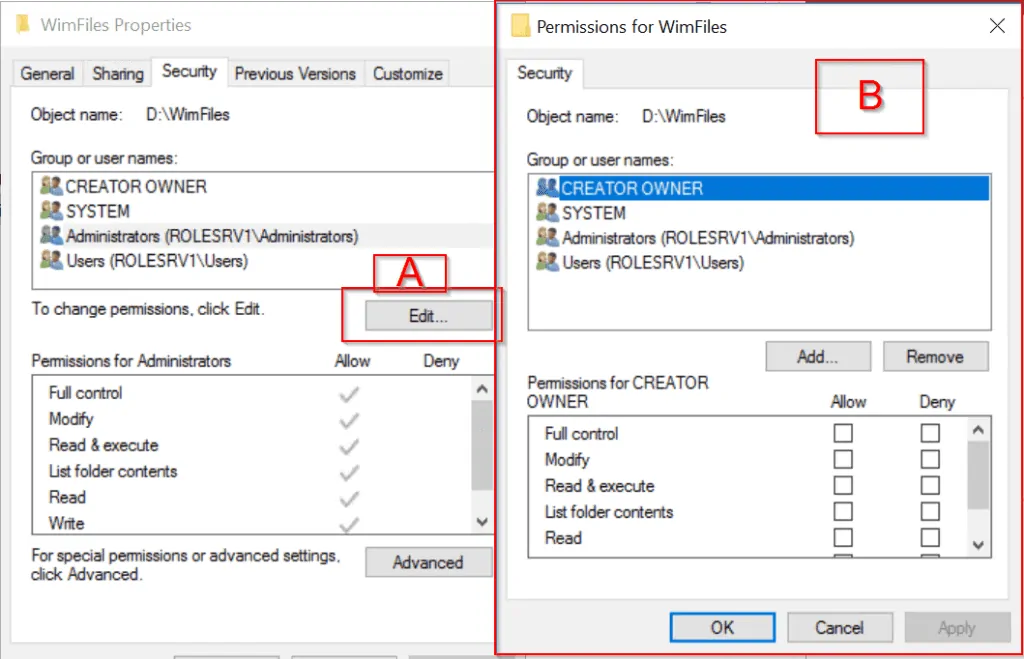
- Click Edit (labelled “A” in the image below). The part labelled “B” opens for editing. You can add a new user using the Add button. You then need to check the box beside the permission type you wish to grant the user (“Allow” or “Deny”).
How to Configure Share Permissions
There are two ways you can configure share permissions. In this section I will cover both.
As both options are accessed via the folder “Sharing” tab, from the properties of the folder, click the Sharing tab.
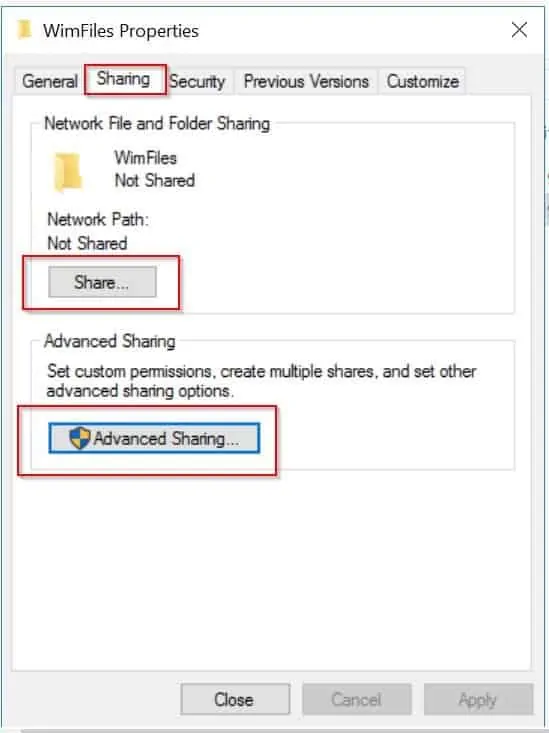
Configure Share Using the “Share” Button
- Click the “Share” button.
- The option to share the folder opens (see image below).
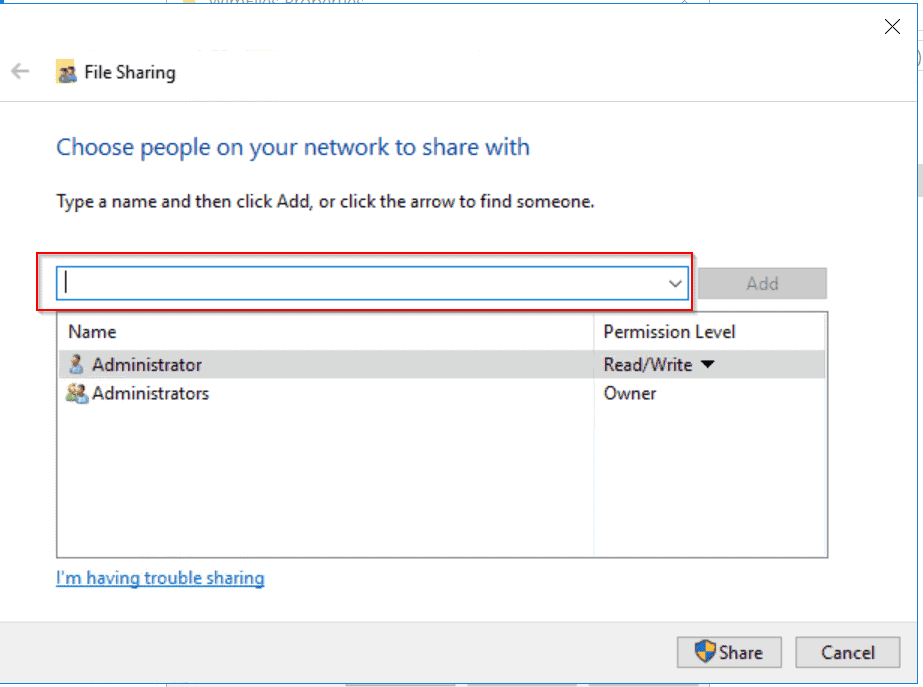
- If you wish to share the folder with the default permissions, click the Share button. Otherwise, to add other users click the drop-down on the highlighted portion of the image. Select Everyone or Find people. Finally, click Add.
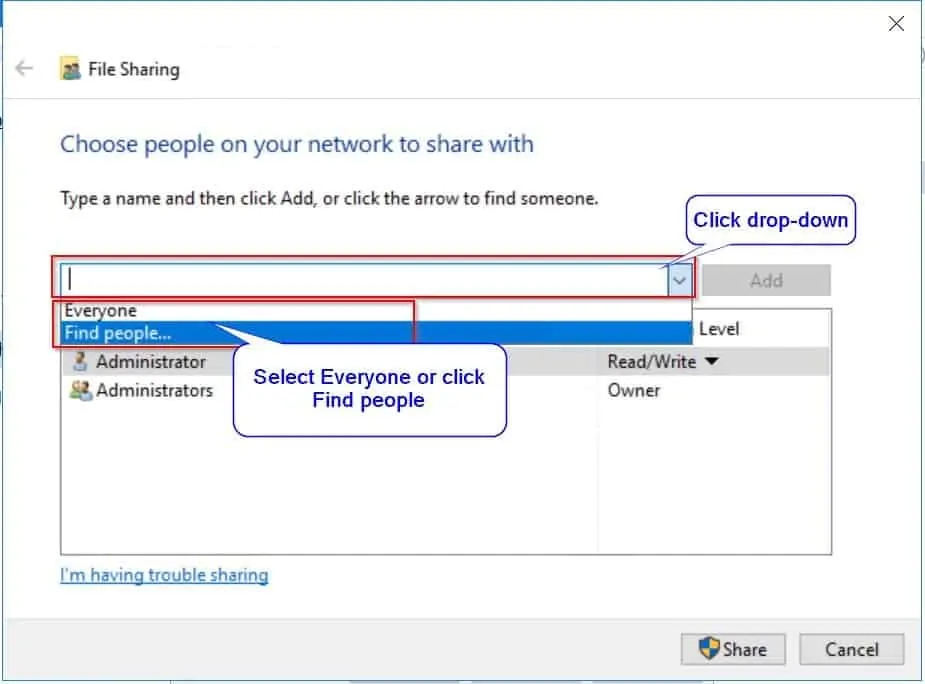
If you select Find people, the system will open the option to search for specific users or groups. See the second image below.
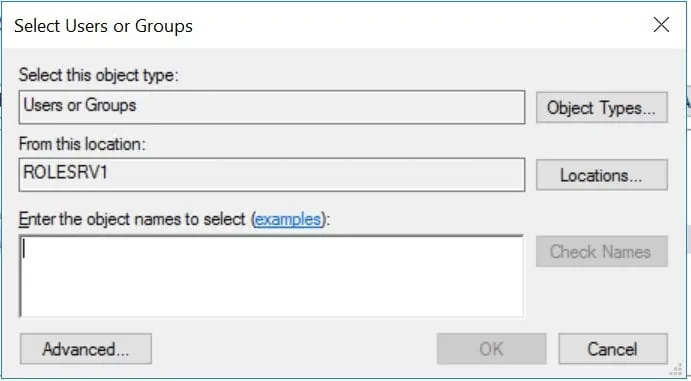
- When you are done adding users or groups and granting the permission you desire, click Share. Review the share information then click Done.

Configure Share Using the “Advanced Sharing” Button

To share using the Advanced Sharing button:
- Click Advanced Sharing button.
- When the Advanced Sharing option loads, check the “Share this folder” box. Accept the default share name or modify it.
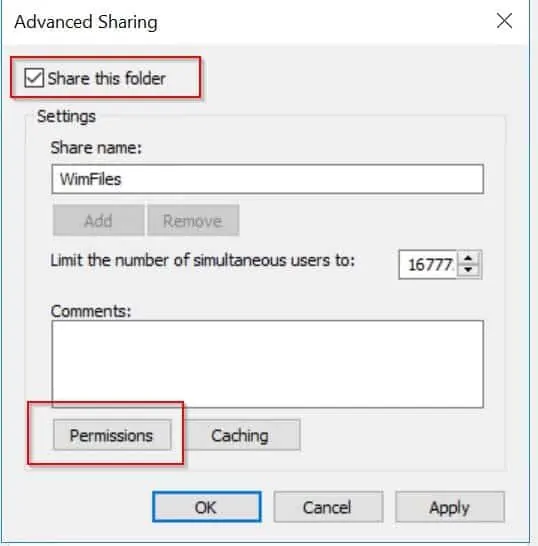
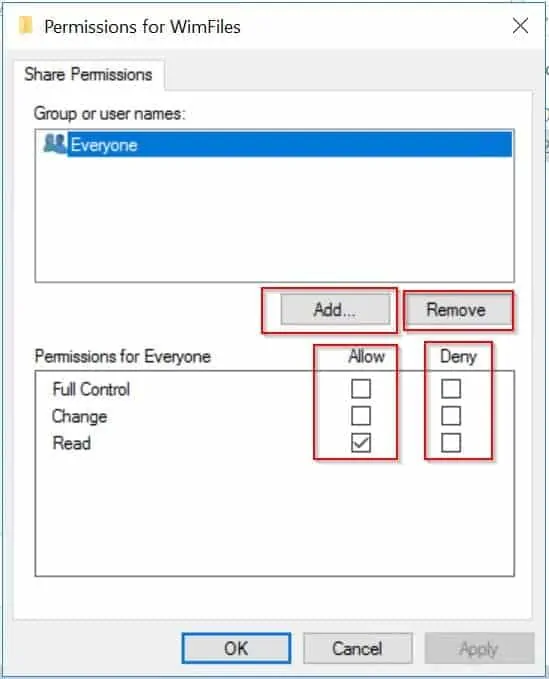
- Then click Permissions. The steps from this point is very similar to the task you performed when you configured NTFS permissions. Add or Remove a user, then check the box beside the permission you wish to grant or deny the user (“Allow” or “Deny”). When you finish, click Ok to share the folder.
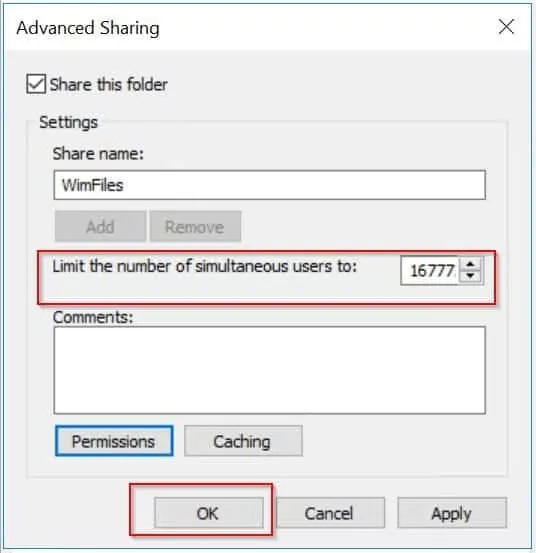
- When you click Ok, above you will be returned to the “Advanced Sharing” page. Here you can configure the number of simultaneous users (concurrent connections). When you finish, click Ok.
- The folder is now shared with the permissions you configured!
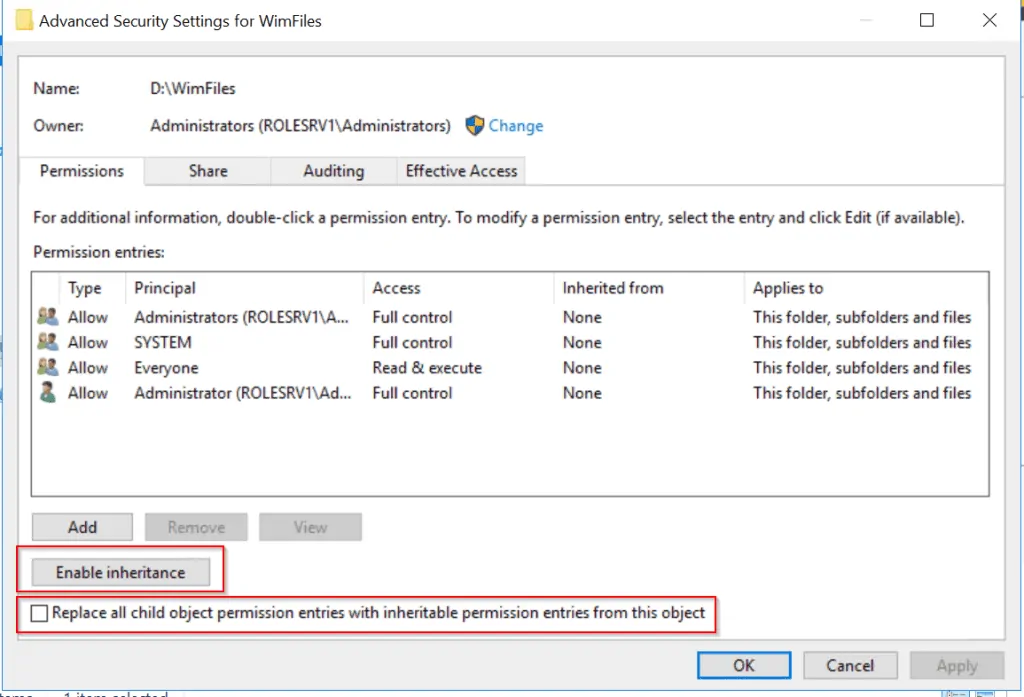
How to Configure NTFS Permission Inheritance
- From the properties page of the folder, click Security.

- To enable NTFS Permissions inheritance, click Enable inheritance. To force the permissions on the top level folder to propagate to all child items, check the box beside Replace all child object permissions entries with inheritable permission entry from this object. Click Ok to apply your changes.
Conclusion
There you have it! NTFS Permissions simplified.
I hope you have added to your knowledge of NTFS and share permissions. If you have, kindly share your experience with our community using the “Leave a Reply” form at the bottom of this page.
Alternatively, you can respond to the “Was this page helpful?” question below.



